@zhangyy
2021-12-01T02:13:40.000000Z
字数 9045
阅读 1088
k8s 1.22.4 二进制部署
kubernetes系列
一: 系统环境初始化
1.1 系统环境
cat /etc/hosts----172.16.10.11 flyfishsrvs01172.16.10.12 flyfishsrvs02172.16.10.13 flyfishsrvs03172.16.10.14 flyfishsrvs04172.16.10.15 flyfishsrvs05172.16.10.16 flyfishsrvs06172.16.10.17 flyfishsrvs07-----先安装单master版本后续扩容成多master系统关闭firewalld/selinux /清空iptables防火墙规则
1.2 升级系统内核
所有机器都要升级内核#查看当前内核版本uname -runame -acat /etc/redhat-release#添加yum源仓库mv /etc/yum.repos.d/CentOS-Base.repo /etc/yum.repos.d/CentOS-Base.repo.backupcurl -o /etc/yum.repos.d/CentOS-Base.repo https://mirrors.aliyun.com/repo/Centos-7.repocurl -o /etc/yum.repos.d/epel.repo http://mirrors.aliyun.com/repo/epel-7.reporpm --import https://www.elrepo.org/RPM-GPG-KEY-elrepo.orgyum install -y https://www.elrepo.org/elrepo-release-7.0-4.el7.elrepo.noarch.rpm#更新yum源仓库yum -y update#查看可用的系统内核包yum --disablerepo="*" --enablerepo="elrepo-kernel" list available#安装内核,注意先要查看可用内核,我安装的是5.4版本的内核yum --enablerepo=elrepo-kernel install kernel-lt#查看目前可用内核awk -F\' '$1=="menuentry " {print i++ " : " $2}' /etc/grub2.cfg#使用序号为0的内核,序号0是前面查出来的可用内核编号grub2-set-default 0#生成 grub 配置文件并重启grub2-mkconfig -o /boot/grub2/grub.cfgreboot
1.2 环境配置
#修改时区,同步时间yum install chrond -yvim /etc/chrony.conf-----ntpdate ntp1.aliyun.com iburst-----ln -sf /usr/share/zoneinfo/Asia/Shanghai /etc/localtimeecho 'Asia/Shanghai' > /etc/timezone#关闭防火墙,selinuxsystemctl stop firewalldsystemctl disable firewalldsed -i 's/enforcing/disabled/' /etc/selinux/configsetenforce 0## 关闭swapswapoff -ased -ri 's/.*swap.*/#&/' /etc/fstab#系统优化cat > /etc/sysctl.d/k8s_better.conf << EOFnet.bridge.bridge-nf-call-iptables=1net.bridge.bridge-nf-call-ip6tables=1net.ipv4.ip_forward=1net.ipv4.tcp_tw_recycle=0vm.swappiness=0vm.overcommit_memory=1vm.panic_on_oom=0fs.inotify.max_user_instances=8192fs.inotify.max_user_watches=1048576fs.file-max=52706963fs.nr_open=52706963net.ipv6.conf.all.disable_ipv6=1net.netfilter.nf_conntrack_max=2310720EOFsysctl -p /etc/sysctl.d/k8s_better.conf#确保每台机器的uuid不一致,如果是克隆机器,修改网卡配置文件删除uuid那一行cat /sys/class/dmi/id/product_uuid
1.3 安装docker
全部节点安装:安装docker这里介绍yum源安装1. 卸载旧版本yum remove docker \docker-client \docker-client-latest \docker-common \docker-latest \docker-latest-logrotate \docker-logrotate \docker-engine \docker-cerm -rf /var/lib/docker2.安装必备软件包yum install -y yum-utils device-mapper-persistent-data lvm23.设置yum源#建议使用阿里源yum-config-manager \--add-repo \http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo4.安装docker这里介绍两种安装方式,我是用的是第一种1)使用yum命令安装#查看可用版本yum list docker-ce --showduplicates | sort -r#安装18.09.1的版本,安装其他版本照套格式就行yum install docker-ce-18.09.1 docker-ce-cli-18.09.1 containerd.io#安装最新版本yum install -y docker-ce docker-ce-cli containerd.iomkdir -p /etc/dockervim /etc/docker/daemon.json-----{"exec-opts": ["native.cgroupdriver=systemd"],"log-driver": "json-file","log-level": "warn","log-opts": {"max-size": "1000m","max-file": "3"},"registry-mirrors": ["https://b9pmyelo.mirror.aliyuncs.com"],"insecure-registries": [],"selinux-enabled": false}
二:部署etcd集群
2.1 关于签名证书
wget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64chmod +x cfssl_linux-amd64 cfssljson_linux-amd64 cfssl-certinfo_linux-amd64mv cfssl_linux-amd64 /usr/bin/cfsslmv cfssljson_linux-amd64 /usr/bin/cfssljsonmv cfssl-certinfo_linux-amd64 /usr/bin/cfssl-certinfo
mkdir -p ~/TLS/{etcd,k8s}cd ~/TLS/etcd自签CA:cat > ca-config.json << EOF{"signing": {"default": {"expiry": "87600h"},"profiles": {"www": {"expiry": "87600h","usages": ["signing","key encipherment","server auth","client auth"]}}}}EOFcat > ca-csr.json << EOF{"CN": "etcd CA","key": {"algo": "rsa","size": 2048},"names": [{"C": "CN","L": "Beijing","ST": "Beijing"}]}EOF生成证书:cfssl gencert -initca ca-csr.json | cfssljson -bare ca -会生成ca.pem和ca-key.pem文件
2. 使用自签CA签发Etcd HTTPS证书创建证书申请文件:cat > server-csr.json << EOF{"CN": "etcd","hosts": ["172.16.10.11","172.16.10.12","172.16.10.13","172.16.10.14","172.16.10.15","172.16.10.16","172.16.10.17","172.16.10.18","172.16.10.19","172.16.10.200"],"key": {"algo": "rsa","size": 2048},"names": [{"C": "CN","L": "BeiJing","ST": "BeiJing"}]}EOF注:上述文件hosts字段中IP为所有etcd节点的集群内部通信IP,一个都不能少!为了方便后期扩容可以多写几个预留的IP。生成证书:cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=www server-csr.json | cfssljson -bare server会生成server.pem和server-key.pem文件。
2.2 部署etcd
1. Etcd 的概念:Etcd 是一个分布式键值存储系统,Kubernetes使用Etcd进行数据存储,所以先准备一个Etcd数据库,为解决Etcd单点故障,应采用集群方式部署,这里使用3台组建集群,可容忍1台机器故障,当然,你也可以使用5台组建集群,可容忍2台机器故障。下载地址: https://github.com/etcd-io/etcd/releases以下在节点1上操作,为简化操作,待会将节点1生成的所有文件拷贝到节点2和节点3.
2. 安装配置etcdmkdir /opt/etcd/{bin,cfg,ssl} -ptar zxvf etcd-v3.5.1-linux-amd64.tar.gzmv etcd-v3.5.1-linux-amd64/{etcd,etcdctl} /opt/etcd/bin/
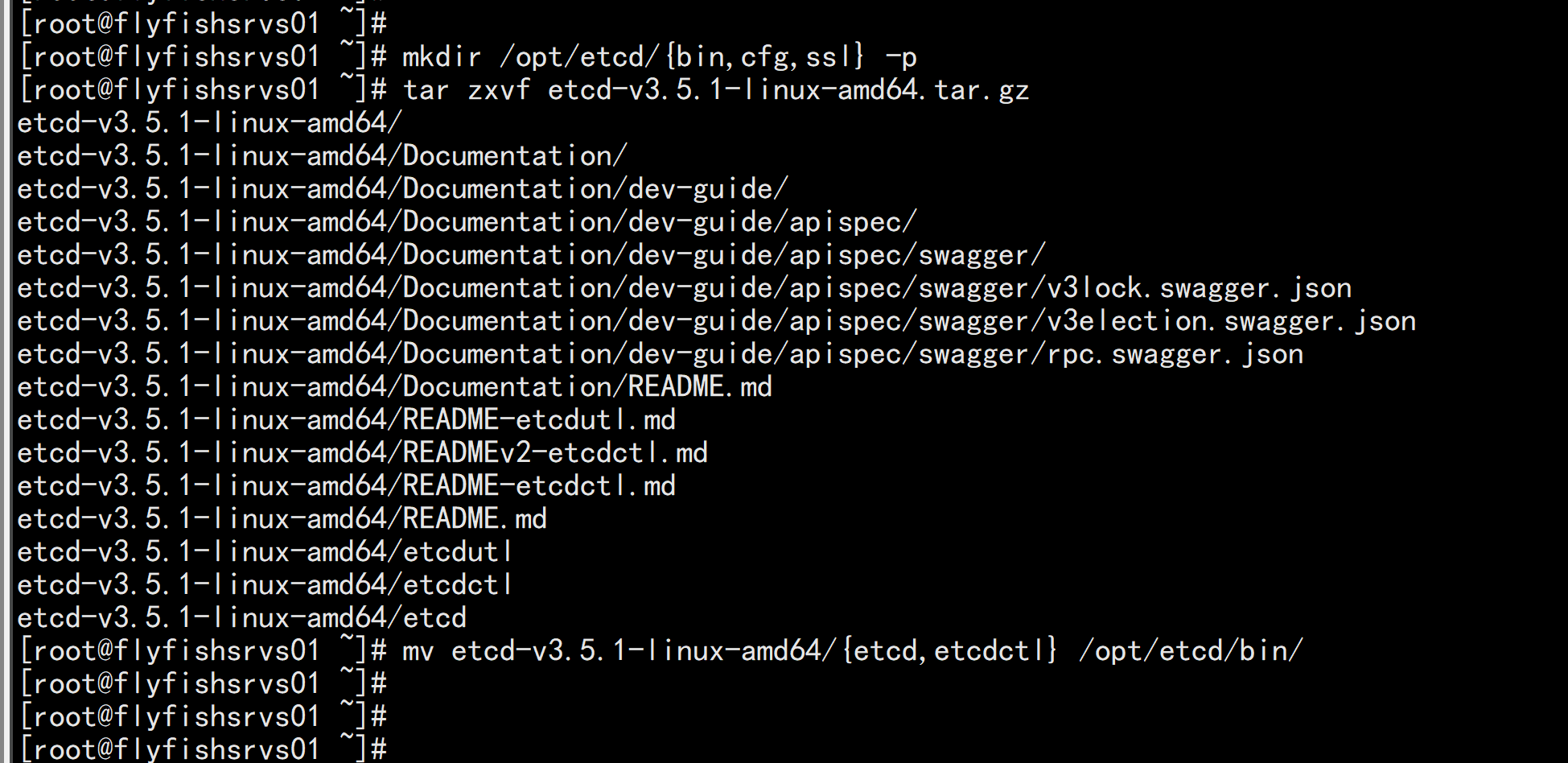
flyfishsrvs01 etcd 配置文件cat > /opt/etcd/cfg/etcd.conf << EOF#[Member]ETCD_NAME="etcd-1"ETCD_DATA_DIR="/var/lib/etcd/default.etcd"ETCD_LISTEN_PEER_URLS="https://172.16.10.11:2380"ETCD_LISTEN_CLIENT_URLS="https://172.16.10.11:2379"#[Clustering]ETCD_INITIAL_ADVERTISE_PEER_URLS="https://172.16.10.11:2380"ETCD_ADVERTISE_CLIENT_URLS="https://172.16.10.11:2379"ETCD_INITIAL_CLUSTER="etcd-1=https://172.16.10.11:2380,etcd-2=https://172.16.10.12:2380,etcd-3=https://172.16.10.13:2380"ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"ETCD_INITIAL_CLUSTER_STATE="new"EOF---ETCD_NAME:节点名称,集群中唯一ETCD_DATA_DIR:数据目录ETCD_LISTEN_PEER_URLS:集群通信监听地址ETCD_LISTEN_CLIENT_URLS:客户端访问监听地址ETCD_INITIAL_ADVERTISE_PEER_URLS:集群通告地址ETCD_ADVERTISE_CLIENT_URLS:客户端通告地址ETCD_INITIAL_CLUSTER:集群节点地址ETCD_INITIAL_CLUSTER_TOKEN:集群TokenETCD_INITIAL_CLUSTER_STATE:加入集群的当前状态,new是新集群,existing表示加入已有集群
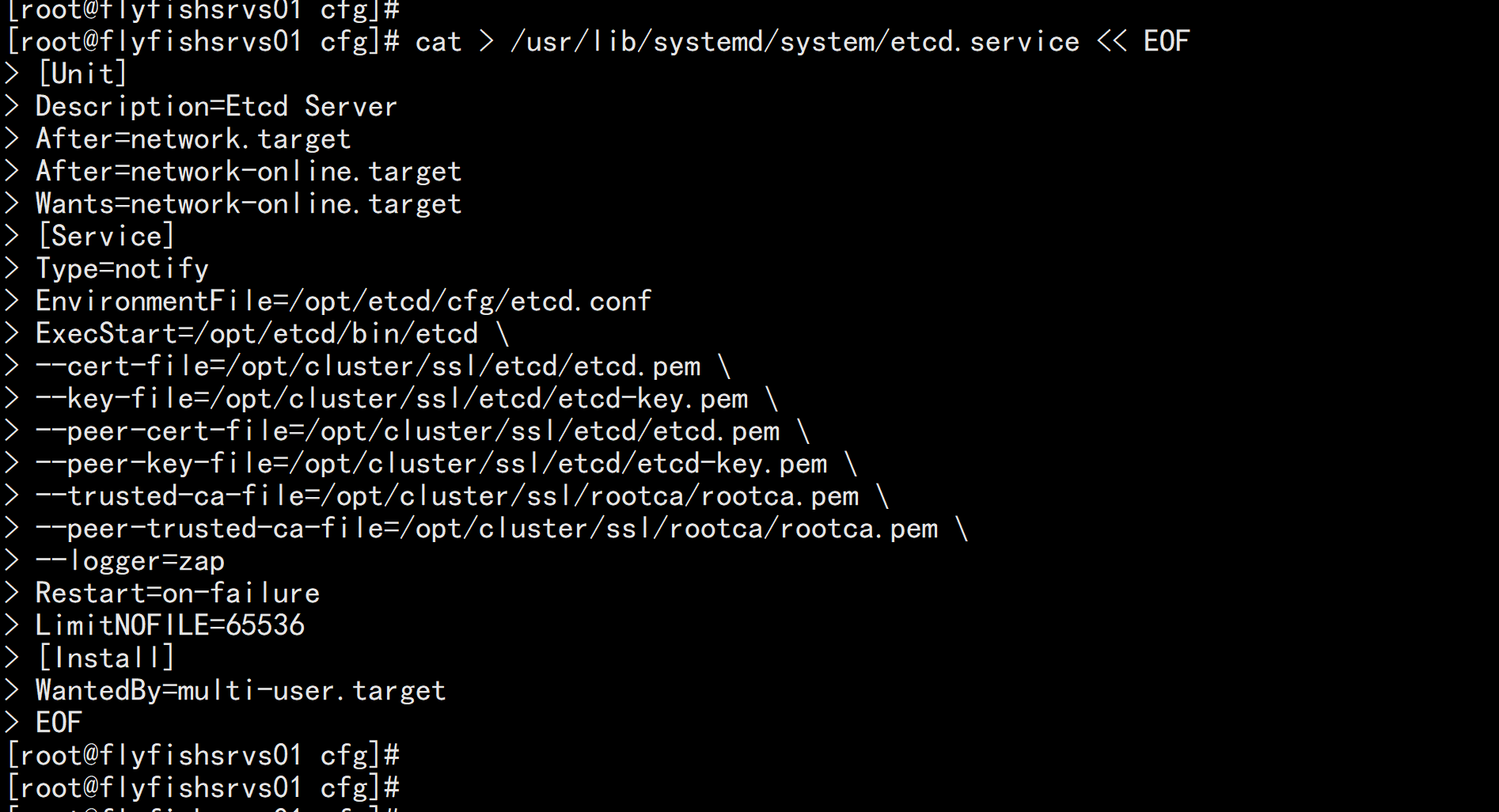
3. systemd管理etcdcat > /usr/lib/systemd/system/etcd.service << EOF[Unit]Description=Etcd ServerAfter=network.targetAfter=network-online.targetWants=network-online.target[Service]Type=notifyEnvironmentFile=/opt/etcd/cfg/etcd.confExecStart=/opt/etcd/bin/etcd \--cert-file=/opt/etcd/ssl/server.pem \--key-file=/opt/etcd/ssl/server-key.pem \--peer-cert-file=/opt/etcd/ssl/server.pem \--peer-key-file=/opt/etcd/ssl/server-key.pem \--trusted-ca-file=/opt/etcd/ssl/ca.pem \--peer-trusted-ca-file=/opt/etcd/ssl/ca.pem \--logger=zapRestart=on-failureLimitNOFILE=65536[Install]WantedBy=multi-user.targetEOF
4. 拷贝刚才生成的证书把刚才生成的证书拷贝到配置文件中的路径:cp ~/TLS/etcd/ca*pem ~/TLS/etcd/server*pem /opt/etcd/ssl/
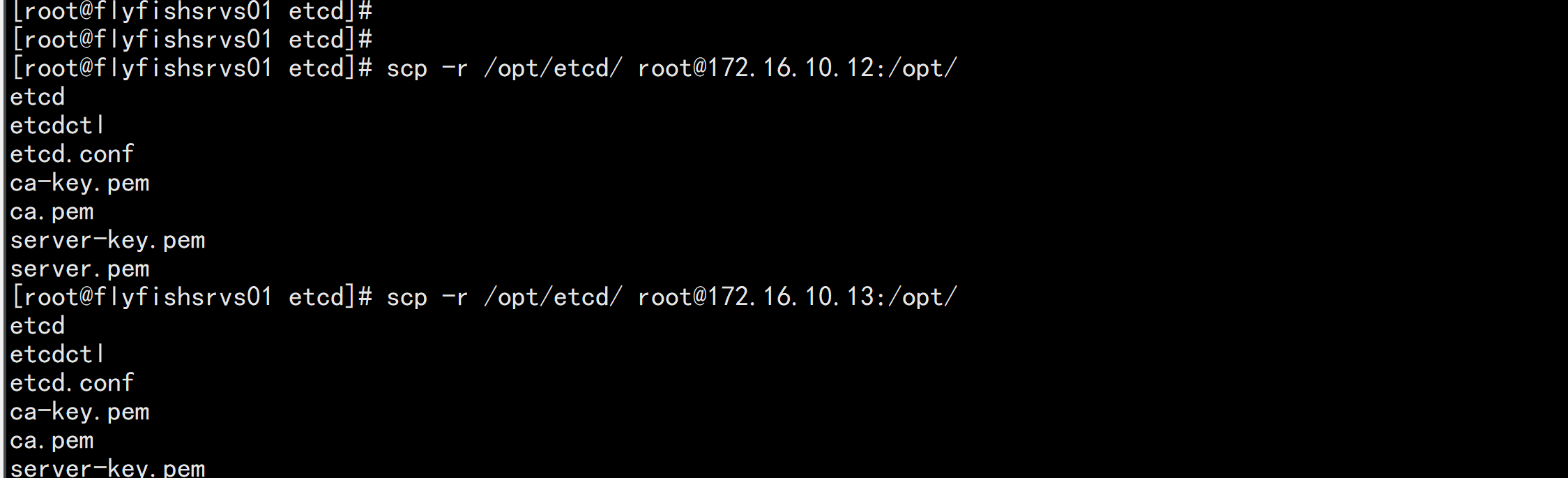
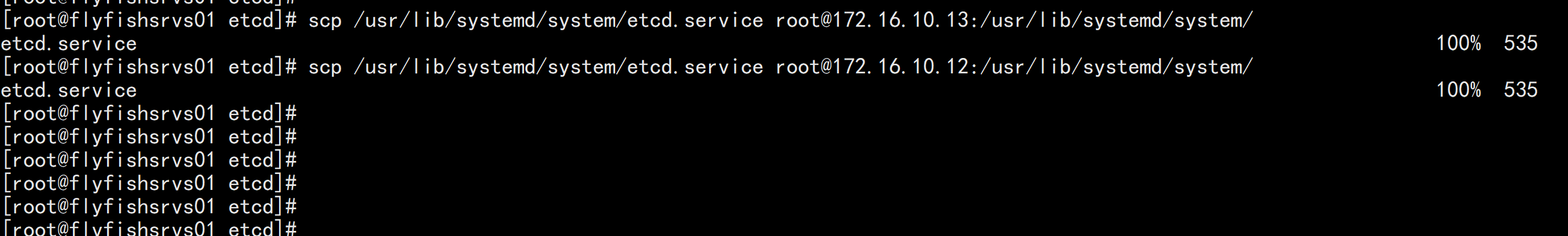
5. 同步所有主机scp -r /opt/etcd/ root@172.16.10.12:/opt/scp -r /opt/etcd/ root@172.16.10.13:/opt/scp /usr/lib/systemd/system/etcd.service root@172.16.10.12:/usr/lib/systemd/system/scp /usr/lib/systemd/system/etcd.service root@172.16.10.13:/usr/lib/systemd/system/
flyfishsrvs02 etcdvim /opt/etcd/cfg/etcd.conf-----#[Member]ETCD_NAME="etcd-2"ETCD_DATA_DIR="/var/lib/etcd/default.etcd"ETCD_LISTEN_PEER_URLS="https://172.16.10.12:2380"ETCD_LISTEN_CLIENT_URLS="https://172.16.10.12:2379"#[Clustering]ETCD_INITIAL_ADVERTISE_PEER_URLS="https://172.16.10.12:2380"ETCD_ADVERTISE_CLIENT_URLS="https://172.16.10.12:2379"ETCD_INITIAL_CLUSTER="etcd-1=https://172.16.10.11:2380,etcd-2=https://172.16.10.12:2380,etcd-3=https://172.16.10.13:2380"ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"ETCD_INITIAL_CLUSTER_STATE="new"----
flyfishsrvs03 etcdvim /opt/etcd/cfg/etcd.conf----#[Member]ETCD_NAME="etcd-3"ETCD_DATA_DIR="/var/lib/etcd/default.etcd"ETCD_LISTEN_PEER_URLS="https://172.16.10.13:2380"ETCD_LISTEN_CLIENT_URLS="https://172.16.10.13:2379"#[Clustering]ETCD_INITIAL_ADVERTISE_PEER_URLS="https://172.16.10.13:2380"ETCD_ADVERTISE_CLIENT_URLS="https://172.16.10.13:2379"ETCD_INITIAL_CLUSTER="etcd-1=https://172.16.10.11:2380,etcd-2=https://172.16.10.12:2380,etcd-3=https://172.16.10.13:2380"ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"ETCD_INITIAL_CLUSTER_STATE="new"-----
6. 启动etcd:systemctl daemon-reloadsystemctl start etcdsystemctl enable etcd
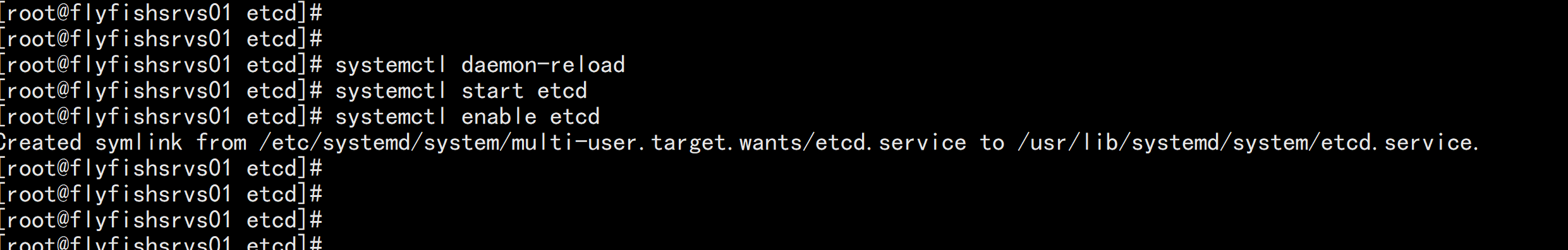
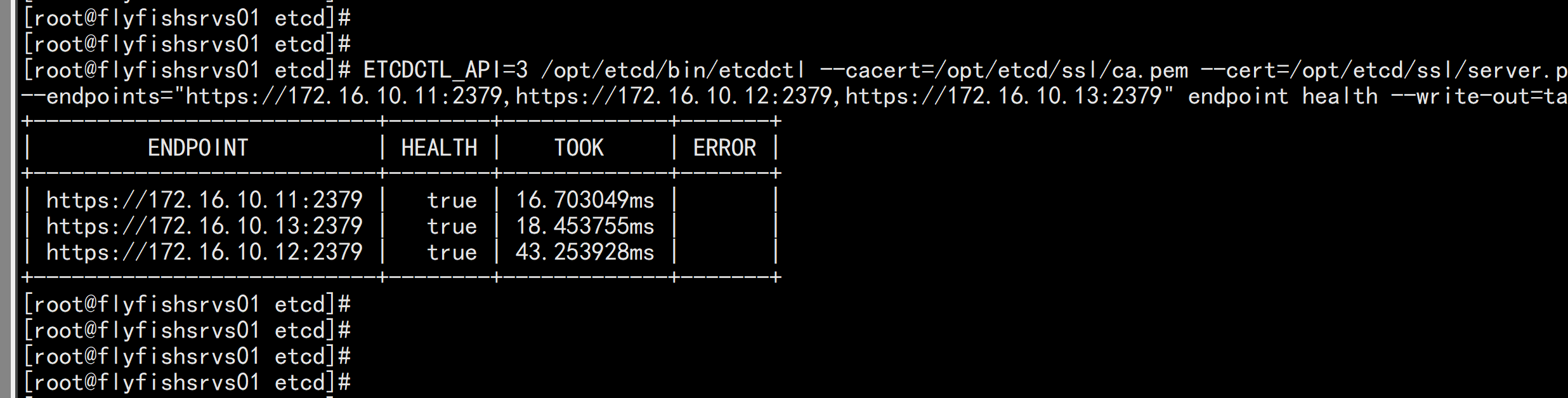
验证:ETCDCTL_API=3 /opt/etcd/bin/etcdctl --cacert=/opt/etcd/ssl/ca.pem --cert=/opt/etcd/ssl/server.pem --key=/opt/etcd/ssl/server-key.pem --endpoints="https://172.16.10.11:2379,https://172.16.10.12:2379,https://172.16.10.13:2379" endpoint health --write-out=table
2.3 部署k8s1.22.4
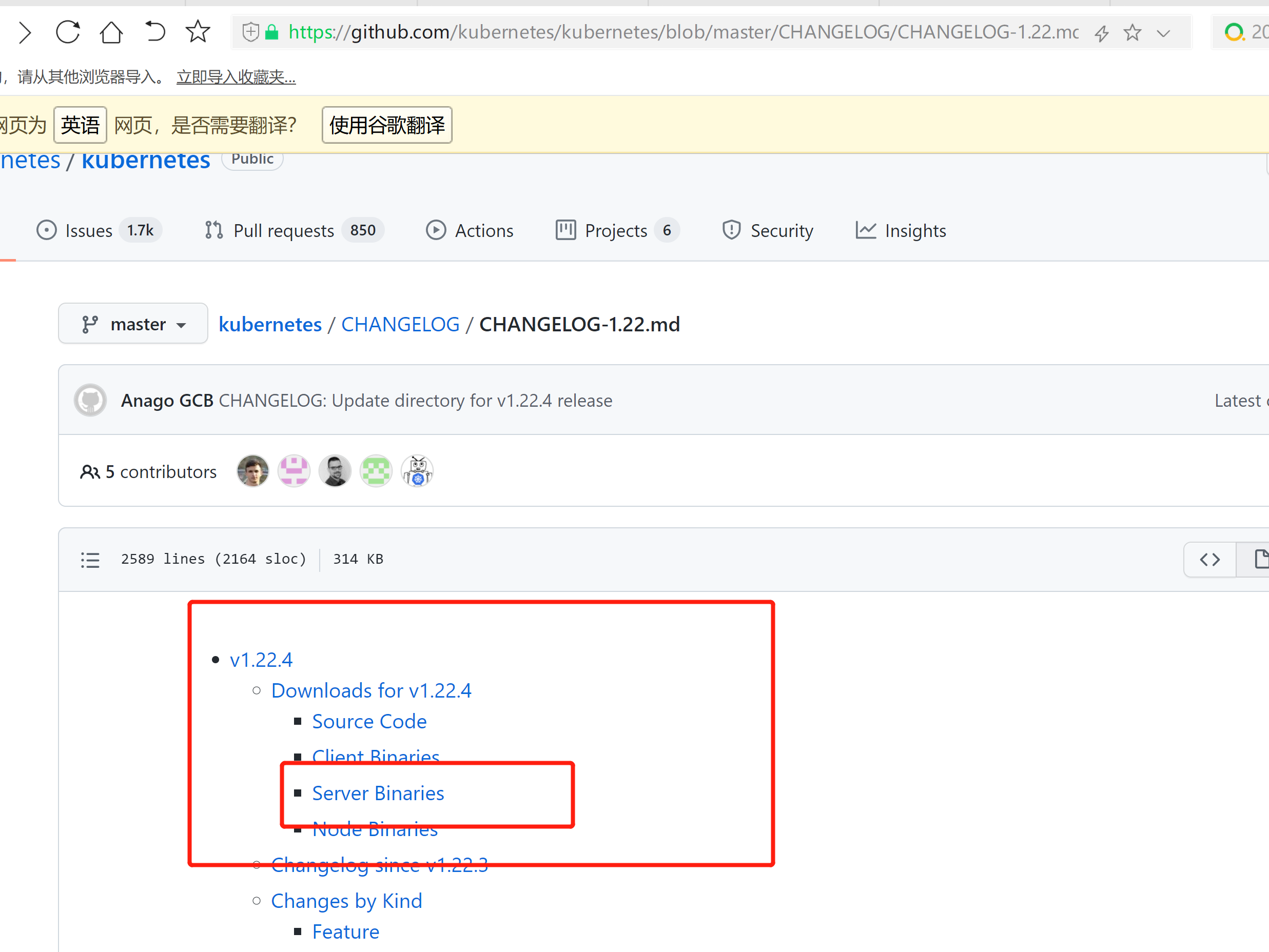
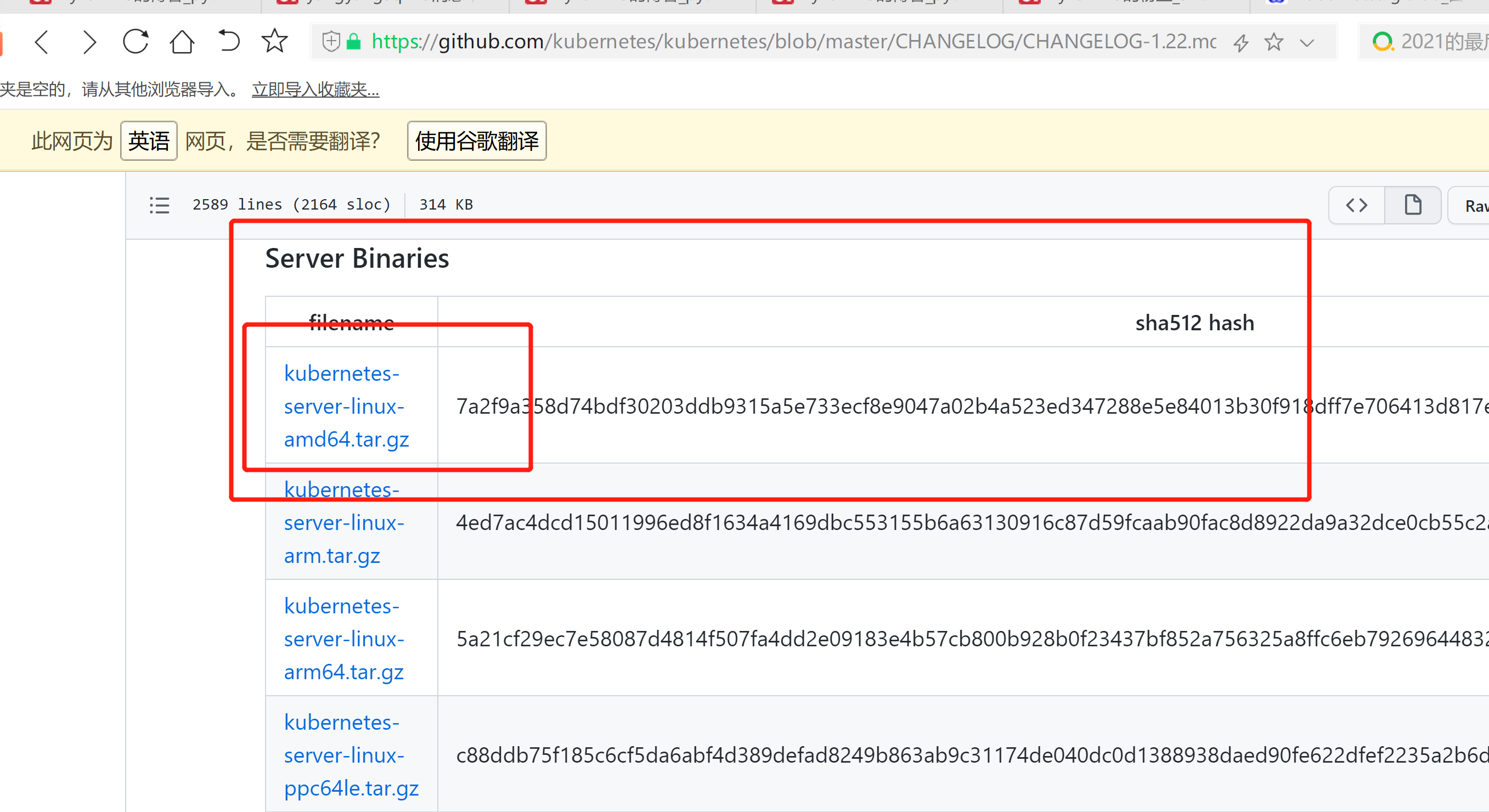
1. 从Github下载二进制文件下载地址: https://github.com/kubernetes/kubernetes/blob/master/CHANGELOG/CHANGELOG-1.22.md注:打开链接你会发现里面有很多包,下载一个server包就够了,包含了Master和Worker Node二进制文件。
2. 创建k8s 的kube-apiserver证书cd ~/TLS/k8scat > ca-config.json << EOF{"signing": {"default": {"expiry": "87600h"},"profiles": {"kubernetes": {"expiry": "87600h","usages": ["signing","key encipherment","server auth","client auth"]}}}}EOFcat > ca-csr.json << EOF{"CN": "kubernetes","key": {"algo": "rsa","size": 2048},"names": [{"C": "CN","L": "Beijing","ST": "Beijing","O": "k8s","OU": "System"}]}EOF生成证书:cfssl gencert -initca ca-csr.json | cfssljson -bare ca -会生成ca.pem和ca-key.pem文件。
2. 使用自签CA签发kube-apiserver HTTPS证书创建证书申请文件:cat > server-csr.json << EOF{"CN": "kubernetes","hosts": ["10.0.0.1","127.0.0.1","172.16.10.11","172.16.10.12","172.16.10.13","172.16.10.14","172.16.10.15","172.16.10.16","172.16.10.17","172.16.10.18","172.16.10.19","172.16.10.200","kubernetes","kubernetes.default","kubernetes.default.svc","kubernetes.default.svc.cluster","kubernetes.default.svc.cluster.local"],"key": {"algo": "rsa","size": 2048},"names": [{"C": "CN","L": "BeiJing","ST": "BeiJing","O": "k8s","OU": "System"}]}EOF注:上述文件hosts字段中IP为所有Master/LB/VIP IP,一个都不能少!为了方便后期扩容可以多写几个预留的IP。cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes server-csr.json | cfssljson -bare server