@cdmonkey
2018-06-12T02:37:19.000000Z
字数 5229
阅读 2331
Tomcat & Springboot-SSL
SSL
http://www.tuicool.com/articles/baeInyu
http://blog.chinaunix.net/uid-17102734-id-2830223.html
http://yaodaqing.iteye.com/blog/790349
https://www.chinassl.net/ssltools/keytool-commands.html
Official documents:http://tomcat.apache.org/tomcat-8.0-doc/ssl-howto.html
两种情况:使用自签名的证书,也可使用第三方证书颁发机构所颁发的证书。
一、Generate Certificate
1. 使用自签名的证书
A. Prepare the Certificate Keystore
我们需使用命令行指令keytool来创建自签名证书。
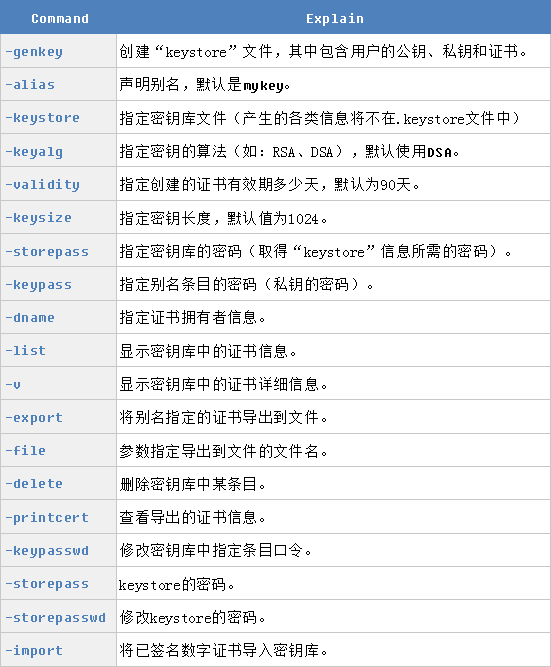
# Remove existing keystore file:[root@Node-A2 ~]# keytool -delete -alias tomcat -keystore tomcat8/cert/server.keystore -storepass "suixingpay"
从头开始创建一个新的密钥库,其中包含一个自签名的证书,需要于终端命令行中执行以下指令:
[root@Node-A2 ~]# keytool -genkey -alias tomcat -keyalg RSA# After executing this command, you will first be prompted for the keystore password.# The default password used by Tomcat is "changeit", although you can specify a custom password if you like:Enter keystore password:Re-enter new password:# Next, you will be prompted for general information about this Certificate:What is your first and last name?[Unknown]: WangWhat is the name of your organizational unit?[Unknown]: suixingpayWhat is the name of your organization?[Unknown]: vbill.cnWhat is the name of your City or Locality?[Unknown]: BeijingWhat is the name of your State or Province?[Unknown]: BeijingWhat is the two-letter country code for this unit?[Unknown]: CNIs CN=Wang, OU=suixingpay, O=vbill.cn, L=Beijing, ST=Beijing, C=CN correct?[no]: y# Finally, you will be prompted for the key password, which is the password specifically for thisCertificate:Enter key password for <tomcat>(RETURN if same as keystore password):
上面的指令会于当前用户的家目录下创建一个新的文件,文件名为.keystore。若希望指定文件的存放路径及文件名称,可使用如下指令:
keytool -genkey -alias tomcat -keyalg RSA -keystore /path/to/my/keystore
若上述创建新的密钥存储的指令执行成功,则你将持有一个包含证书的keystore文件能够供服务器使用。
导出证书
首先将证书进行导出,以使客户端能够将该证书导入:
# Export public key (certificate) from a keystore file:keytool -export -alias 1 -keystore sso.vbill.cn.jks -rfc -file server.cer
B. Edit the Tomcat Configuration File
[root@Node-A2 ~]# vim tomcat8/conf/server.xml<!-- 修改对应连接器的配置内容(指定证书存储文件及其密码):--><Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol"maxThreads="150" SSLEnabled="true" scheme="https" secure="true"clientAuth="false" sslProtocol="TLS"keystoreFile="/root/.keystore"keystorePass="suixingpay" />
修改完上面的设置文件后重启服务,就可以使用“https”安全连接了。我们可以通过如下指令将证书导出:
[root@Node-A2 ~]# keytool -export -alias tomcat -keystore /root/.keystore -file tomcat.crtEnter keystore password:Certificate stored in file <tomcat.crt> #提示导出成功。
导入证书
keytool -import -keystore /home/app/JDK1.8/jre/lib/security/cacerts -file /home/app/keys/sso.suixingpay.com.crt -storepass changei
报错信息:
[app@test-bpm keys]$ keytool -import -keystore /home/app/JDK1.8/jre/lib/security/cacerts -file /home/app/keys/sso.suixingpay.com.crt -storepass changeikeytool error: java.io.IOException: Keystore was tampered with, or password was incorrect
原因是于指定目录下cacerts文件已经存在,备份后移除,再执行命令即可。
2. 使用证书颁发机构签发的证书
这里就会用到我们最开始通过证书颁发机构(CA)签发的那个证书了。
3. Using 443 Port
[root@appxiazai ~]# setcap cap_net_bind_service+ep /home/app/jdk1.8/bin/java[root@appxiazai ~]# getcap /home/app/jdk1.8/bin/java/home/app/jdk1.8/bin/java = cap_net_bind_service+ep
修改完指定指令文件的能力后,就无法启动“Java”进程了。出现如下报错:
[app@appxiazai ~]$ java -versionjava: error while loading shared libraries: libjli.so: cannot open shared object file: No such file or directory
[app@appxiazai ~]$ keytool -import -trustcacerts -alias root -file tomcat8/cert/server_cert.crt -keystore tomcat8/server.keystoreEnter keystore password:Re-enter new password:Owner: OU=network, O=vbill.cn, EMAILADDRESS=wang_hz@suixingpay.com, C=CN, ST=China, CN=www.vbill.cnIssuer: O=Root Certification Authority, EMAILADDRESS=test@cert.com, C=CN, ST=HZ, CN=My Test CASerial number: 1Valid from: Tue Dec 22 11:00:10 CST 2015 until: Wed Dec 21 11:00:10 CST 2016Certificate fingerprints:MD5: 84:68:78:C3:50:54:21:C9:77:88:AC:3D:0F:9A:D3:ABSHA1: F8:37:CB:77:51:38:95:AB:BC:5C:FA:90:BA:02:BA:5C:26:1C:32:BFSHA256: F9:A8:99:02:0F:EB:9A:BA:2F:F4:8E:5E:8C:E2:59:78:45:E0:76:26:ED:A5:E1:64:64:EF:2E:FC:B5:47:CD:68Signature algorithm name: MD5withRSAVersion: 3Extensions:#1: ObjectId: 2.5.29.19 Criticality=falseBasicConstraints:[CA:falsePathLen: undefined]Trust this certificate? [no]: yCertificate was added to keystore
[app@appxiazai ~]$ keytool -list -keystore tomcat8/server.keystoreEnter keystore password:Keystore type: JKSKeystore provider: SUNYour keystore contains 1 entryroot, Dec 22, 2015, trustedCertEntry,Certificate fingerprint (SHA1): F8:37:CB:77:51:38:95:AB:BC:5C:FA:90:BA:02:BA:5C:26:1C:32:BF
# Check the contents of a keystore:[app@SSO2 key]$ keytool -list -v -keystore sso.keystoreEnter keystore password:Keystore type: JKSKeystore provider: SUNYour keystore contains 1 entryAlias name: ssoCreation date: Jun 13, 2016Entry type: PrivateKeyEntryCertificate chain length: 1Certificate[1]:Owner: CN=ma, OU=suixingpay.com, O=sso, L=Beijing, ST=Beijing, C=CNIssuer: CN=ma, OU=suixingpay.com, O=sso, L=Beijing, ST=Beijing, C=CNSerial number: fd28ab9Valid from: Mon Jun 13 09:40:25 CST 2016 until: Sun Sep 11 09:40:25 CST 2016Certificate fingerprints:MD5: 2A:34:50:7B:E5:4B:57:E4:6B:E5:03:4E:6A:95:9D:53SHA1: 79:17:9E:54:F2:15:83:72:79:0C:56:C3:65:5A:A4:B6:A8:AF:B2:43SHA256: 0F:29:2F:92:56:AC:66:9C:FD:3D:C2:E4:89:0F:80:0C:EA:06:F9:7E:0E:91:D5:4D:79:72:A2:DA:E2:3A:8A:BDSignature algorithm name: SHA256withRSAVersion: 3Extensions:#1: ObjectId: 2.5.29.14 Criticality=falseSubjectKeyIdentifier [KeyIdentifier [0000: 51 1D CD 45 BD 42 C6 3C 69 27 5C AE 95 2D EE 99 Q..E.B.<i'\..-..0010: F4 0B B0 33 ...3]]**************************************************************************************
